A growing SaaS company wanted to modernize its cloud deployment process for a full-stack application. They required a cloud native platform that could handle rapid feature delivery with stronger security and faster deployment cycles. They chose AWS as the foundation with Terraform for infrastructure automation and GitHub Actions for CI/CD orchestration.
Our aim was to make their vision a reality. To do so, we built a fully automated Infrastructure as Code (IaC) and deployment pipeline. It brought together infrastructure provisioning and application deployment along with security under one workflow. With automated compliance practices and infrastructure as code, the company cut deployment time from 2 hours to less than 10 minutes. They now release updates multiple times a day with zero downtime and full confidence in production quality.
The team created cloud resources manually. This led to inconsistent environments and configuration drift. Development, staging, and production ended up with different setups, which often caused deployment failures.
Manual deployment processes requiring multiple steps across the frontend and backend increased error rates and deployment time. Each release took 2+ hours with frequent rollbacks.
Long-lived AWS credentials stored in various locations created security risks. No centralized secret management led to credential leaks and compliance issues.
Lack of deployment history and rollback capabilities made troubleshooting difficult. Teams had no clear audit trail of infrastructure or application changes.
Without version control for infrastructure, environments diverged over time. This resulted in "works on my machine" problems and production incidents.
Manual tracking of infrastructure changes made it difficult to maintain audit trails and demonstrate compliance with security standards.
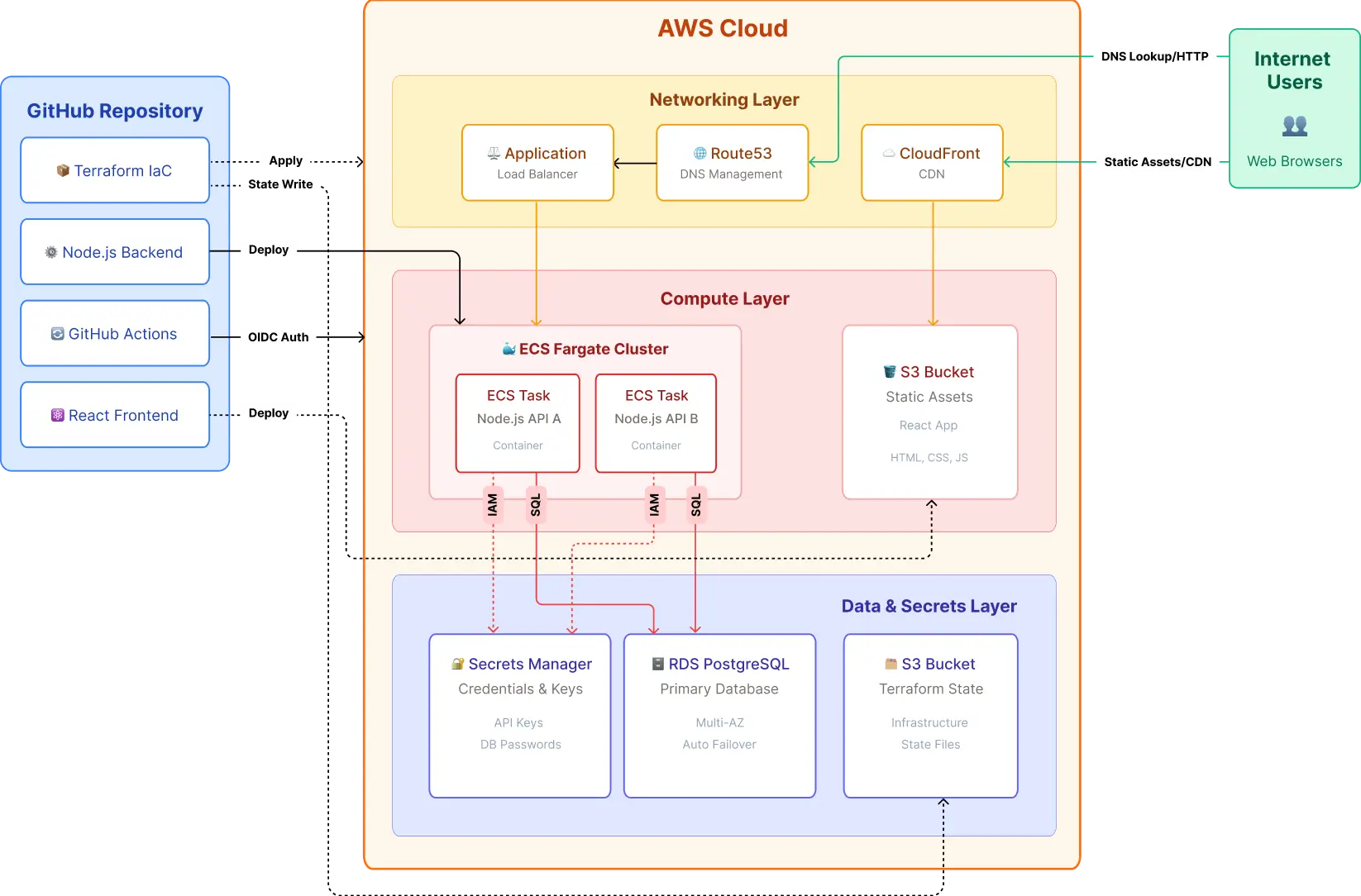
The company implemented a comprehensive automation framework that unified infrastructure provisioning and application deployment. This created a single, automated workflow built entirely on GitHub Actions and AWS.
| Layer | Technology | Purpose |
|---|---|---|
|
Frontend |
React SPA |
Single-page application with modern UI |
|
Backend |
Node.js |
RESTful API with microservices architecture |
|
Infrastructure |
Terraform |
Automated AWS resource provisioning |
|
Container Registry |
Amazon ECR |
Docker image storage and versioning |
|
Compute |
Amazon ECS Fargate |
Serverless container hosting for backend |
|
Database |
Amazon RDS PostgreSQL |
Managed relational database with Multi-AZ |
|
Storage & CDN |
Amazon S3 + CloudFront |
Static asset hosting and global distribution |
|
CI/CD |
GitHub Actions |
Automated build, test, and deployment |
|
Security |
AWS Secrets Manager, IAM |
Secure credential storage and authentication |
|
Monitoring |
CloudWatch |
Application and infrastructure observability |
Every code commit triggered a multistage automated deployment pipeline. It ensured quality and security before production.
AWS Secrets Manager and Parameter Store kept credentials out of the code. The system rotated database passwords every thirty days.
IAM user credentials with configured profiles ensure secure access to AWS resources. Credentials managed securely through GitHub Secrets.
VPC with public and private subnets. Security groups restricted access based on least privilege. Database isolated in private subnet.
RDS encryption at rest with KMS. TLS/SSL for all data in transit. S3 bucket versioning and encryption enabled.
Infrastructure scanned for compliance violations before deployment. Automated alerts for configuration drift. Complete audit trail in CloudTrail.
Vulnerability scanning before deployment. Non-root containers with read-only filesystems. Resource limits enforced on all containers.
| Month | Milestone |
|---|---|
|
1 |
Discovery, toolchain selection, and AWS architecture design |
|
2 |
Terraform infrastructure modules and state backend setup |
|
3 |
GitHub Actions pipeline design and configuration |
|
4 |
Application containerization and ECS deployment |
|
5 |
Security scanning integration and compliance validation |
|
6 |
Production cutover, monitoring setup, and team handover |
Treating infrastructure and application deployments as code with Git version control reduced deployment errors by 98%.
IAM user credentials stored securely in GitHub Secrets with profile-based configuration simplified access management.
DynamoDB-backed state locking prevented concurrent modifications and state corruption, ensuring infrastructure consistency.
ECS blue-green deployments with automated health checks allowed production updates without service interruption.
Integrating security scanning in CI/CD caught vulnerabilities before deployment.
CloudWatch dashboards and X-Ray tracing reduced the mean time to recovery from 4 hours to 15 minutes.
The SaaS company successfully transformed its cloud deployment process. This helped them build a fully automated software delivery ecosystem. They brought together infrastructure automation, continuous deployment, and security monitoring. This completely changed the way their platform operates in the cloud.
The combination of Terraform for infrastructure management and GitHub Actions for CI/CD automation delivered measurable business value. Teams can now deploy with confidence multiple times per day, maintain complete security compliance, and respond to customer needs faster than ever before.