Business trends have been changing drastically in the past year. The global coronavirus pandemic is largely responsible for this shift towards digital business transformation.Business offices have been forced to accept a large number of changes as the norm- working from remote locations, preference for people-centric work, planning the right digital workspace strategy, and many more. The recovery of the entire workforce can be drastically sped up by adopting a bring your own device policy(BYOD).
What is BYOD?
BYOD is better known as Bring Your Own Device. This IT policy promotes providing employees with access to office/work networks using their own electronic devices. With digital business transformation, demand for BYOD has skyrocketed over the past few years. Estimates suggest a global BYOD market surpassing USD 350 billion by 2022. The rise is significant, compared to the 2014 global valuation of USD 94.5 billion in 2014.
A significant factor behind this rapid growth is the improvement in the service network quality. 4G LTE services are available in both developing and developed nations. Other possible reasons include the availability of affordable smartphones and tabs. The BYOD market in North America had already crossed USD 25 Billion in 2013. The trend will likely continue- with the rest of the world catching up quickly. The global pandemic highlighted one of the prime advantages of the BYOD policy- the facility of the “work from home” option.
The Merits and Demerits of BYOD
BYOD has played a vital role in the transition to a digital workforce environment. Here are some of the benefits of implementing BYOD.
Merits:
Higher Productivity
Human behavioral patterns suggest a better grasp and readiness in adopting new technologies under comfortable conditions. Employees feel much more confident and secure in handling their devices than the ones allotted by the organization. This leads to a boost in the efficiency and productivity of any organization.
Improved Employee Morale and Job Satisfaction
In a nutshell, the BYOD policy permits the usage of Enterprise networks and resources through Employee devices. Allowing the employees to choose their preferred device brings a higher level of job satisfaction and contentment.
Higher Savings through Inventory Cutting
With employees relying on their devices (laptops, tablets, or smartphones) for work, organization enterprises can divert their resources elsewhere- improving the overall job experience. Also, BYOD promotes mobility- the work can be carried out from anywhere and everywhere- as long as there is an active internet connection.
Enticing and Attracting Recruits
With remote working locations gaining global popularity, it is easier than ever to recruit the ideal candidates. Forget about the local, or national talent pool. The entire world can be reached within a click.
Demerits:
Security Issues/Concerns
Most critics of the BYOD policy will raise concerns regarding the possibility of a cybersecurity breach. Employees accessing the high sensitive Enterprise data/network using their home pc/laptop/smartphone poses a big risk. The possibility of a device being lost/stolen containing valuable information can never be fully neglected.
Attack from Malware/Spyware or Virus
A system under attack from harmful computer entities is highly vulnerable. Sensitive information may become public knowledge, revealing all the trade secrets. Also known as Data exfiltration, the information may also get stolen/lost.
Device Compatibility Issues
One of the main advantages is adhering to a BYOD policy is reduced hardware cost for the Enterprise. However, this is valid only if the device owned by the employee is capable of handling the requirements. Certain software operates on a specific OS, which may not be compatible with the employee’s device. The device may also lack a proper firewall and other appropriate security measures required by the Enterprise.
Refusal to Grant Company Access by the Employee
Devices commissioned by the organization allow direct control by the Enterprise. However, the employee owning their device may refuse direct access to the Enterprise to protect personal information on the device. This proves problematic if wiping the entire data is deemed necessary, as it will erase both the Enterprise and the employee data.
BYOD Implementation in Organizations
Workforce operation and management have changed drastically during COVID-19. Organizations began to realize that allowing their employees to work from home is essential for both business operations and further prevention of the highly contagious coronavirus. The Bring Your Own Device policy also had a bonus in the availability of skilled manpower from remote and distant locations. Studies indicate 83% of the digital workforce consists of full-time employees. Meanwhile, the percentage of active part-time employees has risen to 11%.
As per a Forbes report, a significant section of the workers believes devices from the workplace have a lower efficiency. The opinion is common among both millennials(61%) and workers above the age of thirty (50%). The report also documents that companies implementing BYOD make an annual saving of USD 350 per employee- while portable devices save up to 58 minutes of employee work-time. Frost & Sullivan reported a productivity increase of 34%.
Here is a list of some popular companies that have implemented BYOD policies to increase their efficiency.
1 INTEL
Intel adopted a BYOD policy in 2009 noting a rising preference for using smartphones and tablets within the workspace network. More than 30000 mobiles are covered under Intel’s BYOD policy- resulting in better overall efficiency. There is also a quick-response system to address BYOD-related queries.
2 SAP
Renowned software services company SAP successfully integrated BYOD policies into its workflow process. SAP has also designed a digital workplace and a mobile platform loaded with several applications. Using a highly-secure system, SAP can wipe a work-device clean in under a minute in case it gets lost or stolen.
3 CYXTERA
Infrastructure company CYXTERA provides safety solutions for BYOD environments. The company provides a global data center platform with advanced cybersecurity features. Its unique AppGate solution, known as the Software-Defined Parameter, can tackle risks posed by the BYOD.
4 3CX
Based on a cloud-based software platform, 3CX utilizes BYOD. The company provides a unified communications system between a business’s partners, workers, and/or customers. The system works flawlessly over any channel, device, or infrastructure.
5 AIRWATCH
The VMware company provides a host of virtualization tools that help its customers implement a BYOD environment. AirWatch provides flexible solutions that protect sensitive corporate data on devices held by the employees.

How BYOD Affects Organizational Effectiveness?
In pen and paper, the possible demerits of a BYOD policy may make it seem not worth the effort. Yet, organizations around the world are rapidly adapting to this IT policy. The advantages are greatly beneficial in increasing the overall efficiency of any organization once set up correctly.
- The efficacy of mobile smartphones and other devices in digital business transformation is verified by statisticians.
- Nearly 3 out of 4 participants in a survey admitted a smartphone is needed for efficient workflow processes.
- The preference for using smartphones as working tools/devices has increased throughout the workforce, especially among millennials.
- Management policies based on BYOD have taken place all over the world - most popular in IT departments.
- Smartphone BYOD is seen as a necessity by giant corporations worldwide, including IBM. IT service providers Unisys and software company Citrix Systems highlighted the emergence of the BYOD model as a trend in 2011.
- A BYOD policy was used by the US Equal Employment Opportunity Commission in 2012, before being swapped out by Blackberrys.
- A 2018 Samsung study revealed that 31% of business enterprises rely completely on BYOD, while approximately 52% of businesses use a customized hybrid approach suited to their needs.
- Around 17% of enterprises provide smartphones/devices to their employees.
- The highest productivity is seen in the organizations adopting a hybrid approach.
- Studies reveal that outsourcing mobile management by major enterprises is getting more and more popular.
10 Tips for Effective BYOD Implementation
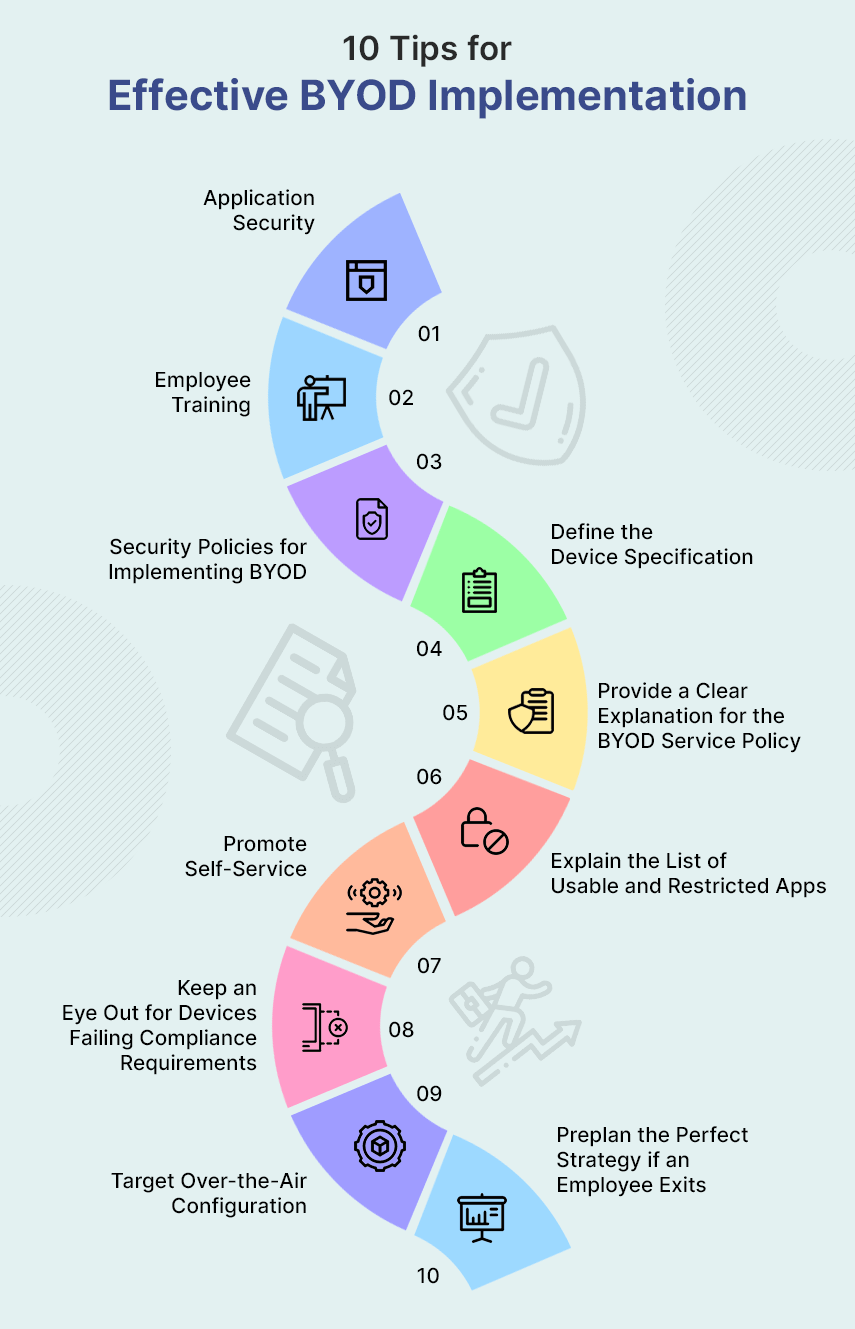
i Application Security
Studies indicate that the security of any BYOD application is of paramount importance. This may be in contrast to the ones developed for device interoperability or system integration- where the function is more important. The security is as critical as the purpose in the case of any BYOD app development.
ii Employee Training
Preserving the security of a BYOD operation is more dependent upon the employees rather than the upper organizational chain-of-command and development. After all, it will be the employees doing most of the regular work through personal devices. Thus, it is essential to ensure that the employees understand the entire BYOD policy, accessibility mechanism, related security, confidentiality, privacy, and boundaries of the mobile digital workspace.
iii Security Policies for Implementing BYOD
A proper framework policy for implementing strict security measures should be done before procuring technology. Users often do not keep any lock screens/passwords on personal devices. Such practices can not be kept up for a prolonged period without some serious implications. Crucial sensitive information may be leaked. An employee opting for the BYOD policy must protect the device with strong and secure passwords instead of the simple 4-letter ones.
iv Define the Device Specification
As an Enterprise, inform the employee about the desired device specifications. Devices may vary upon the manufacturer, hardware components, OS, and many more. The details of the device specifications should be understood by the employees. An iPhone has a different OS than Android. Similarly, Blackberries function differently from the rest. It is necessary to spell out the Enterprise’s requirements in a clear manner.
v Provide a Clear Explanation for the BYOD Service Policy
The business organization needs to resolve issues for the BYOD devices owned by employers. The possible issues that need resolution include support for personal devices owned by employees. Other service policies such as the ones in case of damage, ticketing issues, helpdesk related problems must also be explained clearly.
vi Explain the List of Usable and Restricted Apps
A rule must be made that explicitly discusses the usable and restricted apps within the organization’s network and servers. The rule should be uniform for both personal and corporate devices. For reference, distinct rules must be made for substitute email applications and VPNs. Depending upon the nature of the organization- social media browsing or remote access applications should also be kept under the rule. An organization might even consider prohibiting the download and installation of these applications in a device containing sensitive corporate intel for security purposes.
vii Promote Self-Service
Self-service can be promoted among device users. For functions such as PIN generation, password setup, geo-location, or wiping- self-service is ideal.
viii Keep an Eye Out for Devices Failing Compliance Requirements
Look out for devices and users attempting to override security measures using ‘jail-break’ like activities. You may address these issues by mentioning the reported discrepancy instances to the specific employee user. There is always the wipe button in case of repeated non-compliance.
ix Target Over-the-Air Configuration
Try completing the BYOD configuration distantly. Send settings, profiles, and credentials directly to the BYOD device. There are mainly two reasons for this suggestion. First, this reduces helpdesk traffic. Secondly, this aids in making policies that restrict access to the applications required, and generate data usage warnings.
x Preplan the Perfect Strategy if an Employee Exits
It is not easy to set things into order in case a BYOD device-carrying employee quits. The device will most likely be containing corporate proprietary information, email access, and applications. Several companies do not grant control/synchronization access to corporate emails. Others conduct an exit interview or an HR checklist to ensure the safety of their corporate secrets often demanding a BYOD-enabled security wipe for added security.
Wrapping Up,
Reports and studies conducted all over the world indicate a higher level of productivity and efficiency with the implementation of a correct BYOD policy for any IT business. Bring Your Own Device policy also has several additional benefits- including reduced hardware costs, enhanced mobility, and the facility of working from remote locations.
With the global pandemic forcing lockdown situations and isolation, implementing a BYOD policy has emerged as the workspace transformation of choice for IT companies worldwide.




 January 7, 2021
January 7, 2021


