Touch ID was introduced in iOS 7 as a means to authenticate the user. However, it was limited to just a few activities such as unlocking the device, using the App Store, using iTunes and authenticating the iCloud keychain.
In iOS 8 two new ways of using “Touch Id” has being introduced.
Touch ID is available only on iPhone 5S, iPhone 6, iPhone 6 Plus, iPad Air 2 and iPad Mini 3
Before learning to implement Touch Id we should know how keychain works.
What is Keychain?
Keychain is a database providing secure storage for passwords, keys, certificates and notes for an individual Apple ID.
An application always has access to its own unique keychain items, and it cannot access any keychain items of other applications.
In the Keychain database each row is known as a Keychain Item. Keychain item has attributes and is composed of encrypted values. Keychain is optimized for small items or secrets to allow it’s efficient use. Each keychain item is protected by the user’s passcode and a unique device secret.
Keychain items are available when the device is unlocked; when the device is locked they become unavailable.
To access Keychain, a security framework is used. It is a set of C based APIs called secItem. So when you send request to access data in keychain, it sends request to process, which is known as securityd. All Keychain interactions happen outside the App process space. Once securityd searches for items in the keychain, it is encrypted but it does not have key to decrypt.To decrypt it needs to send the item to Secure Enclave. (Secure enclave is a security code processor built on top of the Apple A7 chip, introduced with the iPhone 5s. Its main operations are to handle all Touch ID operations. It also handles all cryptographic operations for data protection). Secure Enclave decrypt the item depending on the state of the device and sends it back to securityd.
When a user takes a backup of iPhone data, the keychain data is duplicated but the secrets in the keychain remain encrypted in the backup. The keychain password is not included in the backup. Therefore, passwords and other secrets stored in the keychain on the iPhone cannot be used by someone who gains access to an iPhone backup. For this reason it is important to use the keychain on iPhone to store passwords and other data (such as cookies) that can be used to log into secure web sites.
Keychain is good for storing user secrets in the database, however, for storing large files Apple provides another interface called Common Crypto. This interface create a bulk encryption key, and then encrypt large files and bulk data, and then stores that bulk encryption key into the Keychain
Keychain API
secItemAdd : It is used to add Item to Keychain. It takes a dictionary containing a set of attributes that describe your Keychain item and the secret you want to protect.
secItemCopy: It is used to retrieve Item from Keychain. It takes a dictionary containing a set of attributes that describe your Keychain item and specify kSecReturnData.
SecItemUpdate: Is used to Update item from Keychain. It takes 2 dictionary – one to specify the attributes of the item that you’re trying to find, and then a second dictionary to specify the changes that you’d like to make to that Keychain item.
SecItemUpdate: Is used to Delete Item from Keychain. It takes a dictionary containing a set of attributes that describe your Keychain item.
Access Control
kSecAttrAccessGroup: This defines which app can access the Keychain.
kSecAttrAccessible: This defines when the device is accessible – AfterUnlock, AfterFirstUnlock, AccessibleAlways etc.
kSecAttrAccess: This is a new access control added to iO8. It defines who can access the Keychain.
Touch ID
Local Authentication
The Local Authentication framework provides facilities for requesting authentication from users with specified security . For example – to request user authentication using Touch Id policies.
Local Authentication API support 2 capabilities.
1. Local Authentication with Keychain service
Applications can access keychain data by successful authentication of users fingerprint/passcode. This works in coordination with the new attribute ACL (Access Control List) that is added to the keychain Service. ACL allows you to set the accessibility and authentication for a keychain Item. There is a new user presence policy SecAccessControl in iOS 8. To use ACL we should be using the SecAccessControl policy and then check the state of the device using kSecAttrAccessibleWhenPasscodeSetThisDeviceOnly
For Example: Applications need access to password or private data item which the application had saved in keychain previously, then Setting attribute kSecAttrAccessibleWhenPasscodeSetThisDeviceOnly for policy secAccessControl will ensure that users will have to authenticate using fingerprint or passcode mechanism whenever application need to use password stored in Keychain.
When Local Authentication is used with keychain, the Local Authentication UI will be presented by iOS. You won’t have to write code for it.
Limitation Of using ACL
- It works only with Foreground Application. Call on background thread is likely to fail.
- ACL protected items are device-only. It cannot be synchronized or backed up.
2. Local Authentication without Keychain service
Application can authenticate user locally before using it. User will be shown with Touch Id & Passcode UI. You must display a text to explain why Authentication is needed. This helps to build trust with the user.
For Example: To use feature of Application, or unlock feature with Parental control etc.
As you might have noticed only Local authentication is available. Mechanism to authenticate user to remote server is not present
Local Authentication functions
- CanEvaluatePolicy: This will simply check to see if the device is capable of accepting Touch ID.
- EvaluatePolicy: This starts the authentication operation and displays the UI, and returns a true or false answer.
- DeviceOwnerAuthenticationWithBiometrics: This is the policy that can be used to show the Touch ID screen..
Limitation Of using Local Authentication
- It works only with Foreground Application. Call on background thread will fail.
- Contrary to the ACL scenario there is no passcode fallback mechanism here, instead you should implement this fallback in your application to allow users to skip the Touch ID authentication.
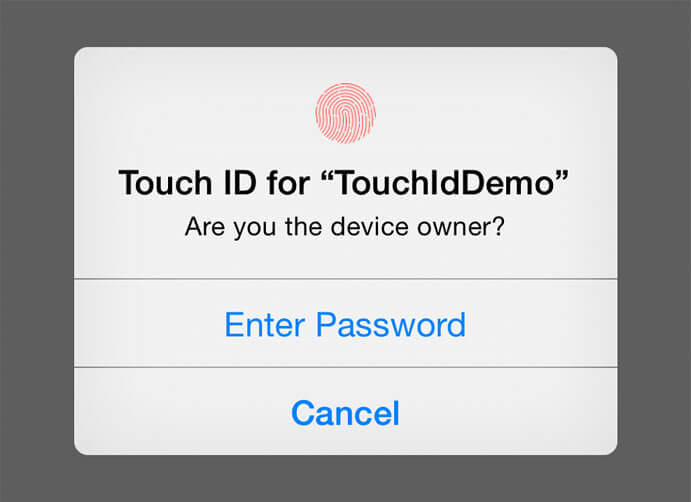
Sample Code to present Touch Id UI for authenticating User. This implementation show Local Authentication without Keychain service as described above. To use Local Authentication with Keychain service you will need to use Apple’s Keychain Wrapper class.
- (void)authenticateButtonTabbed {
LAContext *context = [[LAContext alloc] init];
NSError *error = nil;
if ([context canEvaluatePolicy:LAPolicyDeviceOwnerAuthenticationWithBiometrics error:&error]) {
// Authenticate User
[context evaluatePolicy:LAPolicyDeviceOwnerAuthenticationWithBiometrics
localizedReason:@"Are you the device owner?"
reply:^(BOOL success, NSError *error) {
if (success) {
} else {
switch (error.code) {
case LAErrorAuthenticationFailed:
NSLog(@"Authentication was not successful, because user failed to provide valid credentials.");
break;
case LAErrorUserCancel:
NSLog(@"Authentication was canceled by user");
break;
case LAErrorUserFallback:
NSLog(@"Authentication was canceled, because the user tapped the password button");
break;
case LAErrorSystemCancel:
NSLog(@"Authentication was canceled by system");
break;
default:
NSLog(@"Authentication Failed");
break;
}
}
}
];
} else {
UIAlertView *alert = [[UIAlertView alloc] initWithTitle:@"Error"
message:@"Device cannot authenticate using TouchID."
delegate:nil
cancelButtonTitle:@"Ok"
otherButtonTitles:nil];
[alert show];
}
Touch ID offers a better user experience service in terms of offering a fool proof security to iPhone users.


