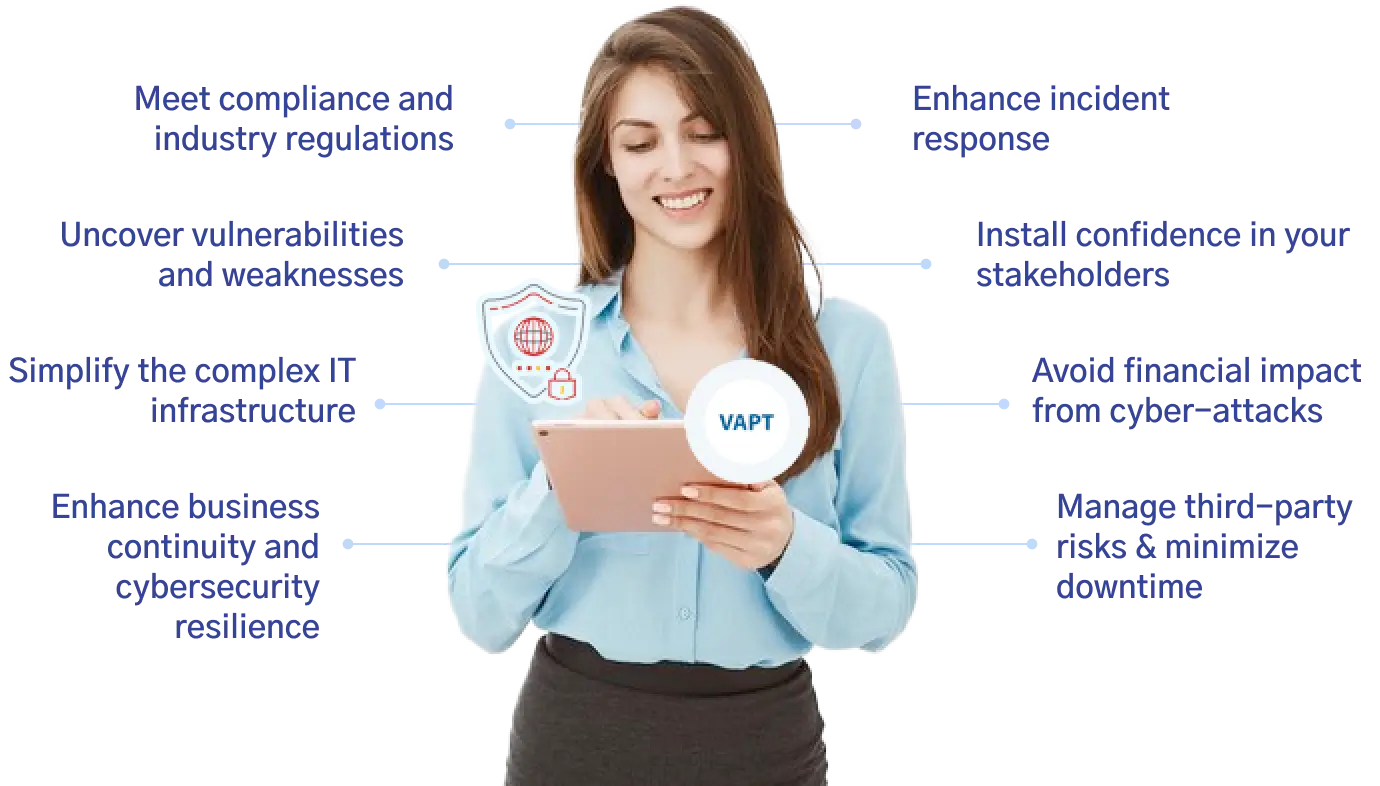
Discovery
Understand the client's business objectives, workflows, and IT
infrastructure.
Scoping
Determine the scope of the assessment, including target systems and
VAPT testing methodologies.
Vulnerability Assessment
Conduct a systematic scan to identify vulnerabilities in
networks, applications, and systems.
Penetration Testing
Simulate real-world attacks to exploit vulnerabilities and assess the
effectiveness of security controls.
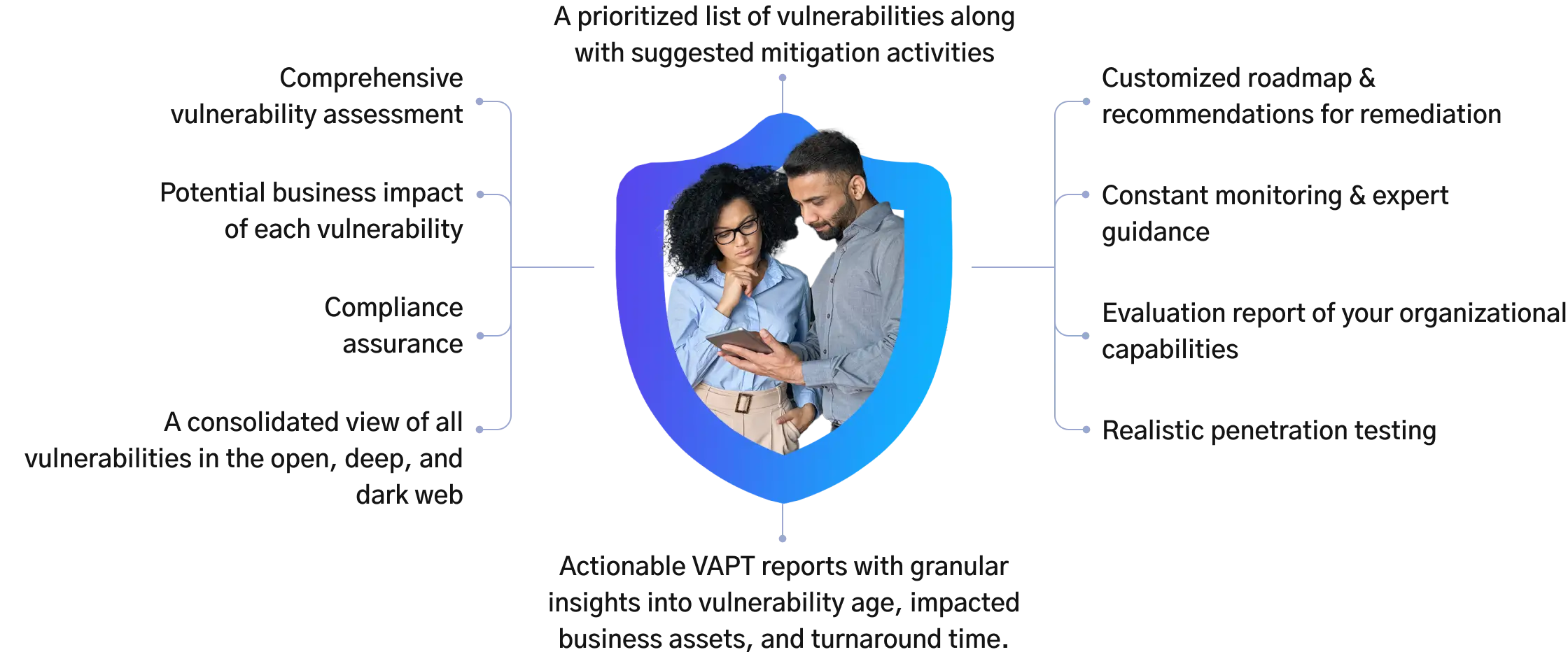
Reporting
Provide comprehensive reports detailing identified vulnerabilities,
their potential impact, and recommended remediation steps.
Remediation Guidance
Collaborate with the client to prioritize and address
vulnerabilities, offering guidance on effective remediation
strategies.
Post-Assessment Support
Offer ongoing support to assist in implementing security enhancements
and monitoring for new threats.
Continuous Monitoring
Deploy VAPT tools and technologies to monitor the client's
infrastructure for emerging threats and promptly respond to
incidents.
Cybersecurity Roadmap
Develop a customized cybersecurity roadmap to address long-term
security needs and align with industry best practices.
Training and Awareness
Conduct cybersecurity awareness programs to educate employees about
potential risks and promote a security-conscious culture.