In 2025, the meteoric growth of mobile applications has made iOS app security more crucial than ever. As cyberattacks on mobile apps have increased more than 80% year-on-year, iOS app developers now face a rapidly evolving threat landscape, with vulnerabilities relentlessly tested by opportunistic attackers and sophisticated threat actors.
Even with the robust ecosystem of Apple and strict app review, recent security scans revealed that most iOS applications still retain serious security vulnerabilities. Hardcoded passwords, weak encryption, mistaken permission settings, and weak security on data storage, all of these may expose consumer information and companies to risk.
Platform-level protection is no longer sufficient as attackers employ AI-driven tools and zero-day attacks to drive and automate their attacks. Right from the start, developers have to step up and incorporate layered iOS app security best practices into the development process to produce compliant, dependable, and secure iOS apps.
As attackers resort to AI-fueled tools and zero-day attacks to fuel and automate their assaults, platform-level protection is no longer adequate. Developers need to integrate layered iOS app security best practices into the development process from the outset, ensuring iOS apps are secure, reliable, and compliant.
Building secure mobile apps starts at the core. A trusted iOS app development company ensures compliance, performance, and long-term user trust.
In this blog, we shall discuss the best practices for securing iOS apps from today's most severe threats.
Top Reasons Why Mobile App Security is Crucial for iOS Development
Protection of Sensitive User Data
iOS apps often process personal information such as passwords, credit card numbers, health records, and private profiles. A lack of adequate data protection exposes it to data breaches, which can lead to identity theft, financial loss, and privacy invasion.
Preventing Data Breaches and Cyberattacks
Strong mobile app security solutions have become the only approach to stop illegal access, malware, and app logic tampering, given the frequency of data theft and breaches.
Maintaining User Trust and Brand Reputation
Users want their information to be secure. Any mobile app security breaches will undermine trust and make users not want to use your app or suggest it to others. User data protection is important to ensure your credibility and foster more adoption.
Compliance with Privacy Laws and Regulations
Including GDPR and CCPA, iOS apps have to abide by international data protection laws. Nonadherence results in app store removal, legal fines, and suspensions from markets.
Leveraging Apple’s Security Architecture
Apple's great security measures, including app sandboxing, boot chain protection, hardware-backed encryption, and biometric authentication, come together to let developers provide secure apps to customers. Although these methods can assist, they might still fall short; developers must use stronger iOS mobile app security measures to stop the growing complexity of assaults.
Partnering with trusted cybersecurity services helps organizations meet GDPR, HIPAA, and CCPA requirements while proactively securing user data.
These services support risk management strategies in all stages of app development.
Mitigating Business and Legal Risks
A data breach might result in consumer base loss, regulatory agency penalties, and lawsuits. Security best practices rule out all these options and enable businesses.
Preventing Reverse Engineering and Unauthorized Modifications
For iOS apps vulnerable to code tampering, reverse engineering, and unauthorized changes, anti-reverse engineering and anti-malicious modification protection are vital. To ensure intellectual property protection and application integrity, mobile app security features, including code obfuscation and runtime protection, are mandated.

Below are critical practices with code examples, pros/cons, and implementation guidelines.
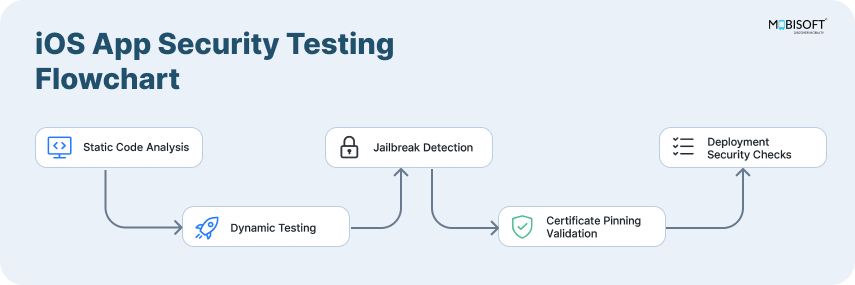
Secure Data Storage with Keychain
Apple's Keychain is the standard for secure data storage iOS solutions of sensitive information in iOS apps. It is specifically built to protect small pieces of sensitive information, such as passwords, tokens, and cryptographic keys, with hardware-driven strong encryption and security controls.
How Keychain Works
Architecture
The Keychain is a single, encrypted SQLite database distributed across the entire system, tightly managed by the 'security' daemon. Any application can access only its own Keychain items, except for access groups that have been set to share between applications by the same author.
Encryption
Everything in the Keychain is encrypted by AES-256-GCM. This operation employs two distinct keys: a metadata key for attributes and a secret key for data content. Always in the custody of the Secure Enclave, the secret key is hardware-backed and protected.
Access Control
The Keychain gives access to sensitive control, so developers can specify the conditions under which things can be accessed, only when the device is unlocked or only on this specific device, for instance.
import Security
// Store a password in the Keychain
func savePassword(username: String, password: String) {
let passwordData = password.data(using: .utf8)!
let query: [CFString: Any] = [
kSecClass: kSecClassGenericPassword,
kSecAttrAccount: username,
kSecValueData: passwordData,
kSecAttrAccessible: kSecAttrAccessibleWhenUnlocked // Only accessible when device is unlocked
]
SecItemDelete(query as CFDictionary) // Remove old item if exists
let status = SecItemAdd(query as CFDictionary, nil)
if status == errSecSuccess {
print("Password saved successfully.")
} else {
print("Error saving password: \(status)")
}
}
// Retrieve a password from the Keychain
func loadPassword(username: String) -> String? {
let query: [CFString: Any] = [
kSecClass: kSecClassGenericPassword,
kSecAttrAccount: username,
kSecReturnData: true,
kSecMatchLimit: kSecMatchLimitOne
]
var dataTypeRef: AnyObject?
let status = SecItemCopyMatching(query as CFDictionary, &dataTypeRef)
if status == errSecSuccess, let retrievedData = dataTypeRef as? Data {
return String(data: retrievedData, encoding: .utf8)
}
return nil
}- kSecClassGenericPassword specifies the item type (password).
- kSecAttrAccount is the username or unique key.
- kSecValueData is the data to store (password).
- kSecAttrAccessibleWhenUnlocked ensures the data is accessible only when the device is unlocked
Pros and Cons of Using Keychain
| Pros | Cons |
| Hardware-backed, strong encryption (AES-256-GCM) | Not designed for storing large data blobs (use Data Protection API for that) |
| Fine-grained access control and sharing options | API can be verbose and complex, especially for error handling |
| Data persists across device reboots and app reinstalls (unless restricted) | Misconfiguration of access controls can lead to security gaps |
| Items can be synchronized securely across devices via iCloud Keychain | Requires careful management of access groups and entitlements for sharing |
Biometric Authentication (Face ID/Touch ID)
The following are the significant reasons for implementing Biometric Authentication, including Face ID and Touch ID, within iOS apps.
Enhanced Security
It uses unique biological features (fingerprint or face) that are exceedingly difficult to duplicate or steal, biometric authentication makes it far more challenging for unwanted access by intruders than passwords or PINs.
By encrypting and storing it safely in the Secure Enclave, never leaving the device unavailable to apps, Apple's design lowers risk even more.
Superior User Experience
Biometrics lets individuals quickly and safely authenticate themselves without needing to recall or input passwords. For apps that need great security, such as banking, health, or password programs, as well as for commonly used applications, this is especially helpful.
Increased User Trust and Adoption
They prefer to use and trust apps that have secure, modern forms of authentication, including Face ID and Touch ID. Real-world situations show that biometric authentication can prevent intruders even in the case of theft.
Regulatory Compliance
A number of privacy laws and security requirements recommend or require robust authentication for such sensitive information. Biometrics are used to meet those demands by providing a secure second factor.
Implementation of biometric authentication requires iOS expertise. Hire iOS app developers to integrate Face ID, Touch ID, and fallback mechanisms effectively.
How to Use Biometric Authentication Properly in iOS App Development
Use Apple’s LocalAuthentication Framework
Apple offers the 'LocalAuthentication' framework, allowing developers to incorporate Face ID and Touch ID easily and securely.
import LocalAuthentication
func authenticateUser() {
let context = LAContext()
var error: NSError?
// Check if biometric authentication is available ( biometrics or passcode)
if context.canEvaluatePolicy(.deviceOwnerAuthentication, error: &error) {
let reason = "Authenticate to access your secure data."
context.evaluatePolicy(.deviceOwnerAuthentication, localizedReason: reason) { success, authenticationError in
DispatchQueue.main.async {
if success {
// Authentication succeeded (biometrics or passcode)
print("User authenticated successfully")
} else {
// Authentication failed
print("Authentication failed: \(authenticationError?.localizedDescription ?? "Unknown error")")
}
}
}
} else {
// No biometrics or passcode set up
print("Authentication not available: \(error?.localizedDescription ?? "Unknown error")")
}
}Always ensure that the authentication prompt has a good and friendly reason string. This will automatically prompt Face ID/Touch ID first, and as a default, request the device passcode (PIN) if not available or fails.
Request User Consent and Be Transparent
- Clearly state why your application uses biometric authentication and how you collect data. This maximizes user trust and adoption.
- Never keep or pass on your biometric information yourself; trust Apple's secure system.
Always Provide a Fallback
- Not all users will have biometrics enabled or available. Always offer an alternative, such as a passcode or password, to ensure accessibility and prevent lockout.
- Implement seamless fallback mechanisms in case biometric authentication fails or is unavailable.
Handle Errors Gracefully
- Notify users of unsuccessful authentications and direct them to the subsequent steps.
- Avoid leaking sensitive information on authentication failure.
Regularly Update and Test
- Stay current with iOS updates to benefit from security improvements and new biometric features.
- Test on different devices and iOS versions for compatibility.
Proactively identifying vulnerabilities requires specialized expertise. You can hire security and penetration testers to run in-depth assessments and secure your iOS app architecture.
Pros and Cons of Biometric Authentication
| Pros | Cons |
| Highly secure (unique to each user, hardware-protected) | Not available on all devices (older iPhones/iPads may lack Face ID/Touch ID) |
| Fast and convenient for users | Some users may be uncomfortable with biometrics or unable to use them (e.g., physical limitations) |
| Reduces reliance on passwords, lowering the risk of phishing and password reuse | Biometric authentication can still be bypassed in rare cases (e.g., sophisticated spoofing) |
| Enhances user trust and app adoption | Requires fallback and careful error handling |
Network Security with SSL Pinning
Why SSL Pinning Is Needed
Protection Against Man-in-the-Middle (MITM) Attacks
Attackers can use stolen networks to display bogus credentials even with HTTPS or take advantage of flaws in certificate authorities (CAs). By guaranteeing the app only trusts a certain certificate or public key, SSL pinning stops illegal connections even if a rogue CA grants a legitimate certificate.
Safeguarding Sensitive Data
iOS apps often transmit sensitive information such as login credentials, financial data, or personal details. Without SSL pinning, attackers could intercept or manipulate this data if they managed to compromise the network or certificate infrastructure.
Ensuring Trust and Compliance
SSL pinning ensures that the application establishes communication with trusted servers only and hence is compliant and keeps the users' trust intact by avoiding data leaks and unauthorized access.
How to Use SSL Pinning Properly in iOS
Understand Pinning Types
Certificate Pinning
Embed the server’s SSL certificate in the app and compare it during each connection. If the server’s certificate changes, the app must be updated with the new certificate.
Public Key Pinning
Save the server's public key in the client. Since public keys do not change much, even upon renewals of the certificates, this approach requires less maintenance.
Implementing SSL Pinning in iOS
Using URLSessionDelegate (Certificate Pinning Example)
class PinningDelegate: NSObject, URLSessionDelegate {
func urlSession(_ session: URLSession, didReceive challenge: URLAuthenticationChallenge, completionHandler: @escaping (URLSession.AuthChallengeDisposition, URLCredential?) -> Void) {
if let serverTrust = challenge.protectionSpace.serverTrust,
let certificate = SecTrustGetCertificateAtIndex(serverTrust, 0) {
let localCert = // Load your bundled certificate as Data
let serverCert = SecCertificateCopyData(certificate) as Data
if localCert == serverCert {
completionHandler(.useCredential, URLCredential(trust: serverTrust))
return
}
}
completionHandler(.cancelAuthenticationChallenge, nil)
}
}The app compares the server’s certificate to the one bundled inside the app. If they match, the connection proceeds; otherwise, it is rejected.
Using Alamofire (Popular Networking Library)
private static func getCertificate(_ filename: String) -> SecCertificate? {
let filePath = Bundle.main.path(forResource: filename, ofType: "cer")
do {
let data = try Data(contentsOf: URL(fileURLWithPath: filePath!))
let certificate = SecCertificateCreateWithData(nil, data as CFData)!
return certificate
} catch {
log.debug("Unable to locate ssl certificate")
}
return nil
}
private static func getSecurityPolicies(certificate: SecCertificate ) -> [String: ServerTrustPolicy] {
let serverTrustPolicy = ServerTrustPolicy.pinCertificates(
certificates: [certificate],
validateCertificateChain: true,
validateHost: true
)
let serverTrustPolicies = [
"app server domain" : serverTrustPolicy
]
return serverTrustPolicies
}
let domain = "app server domain"
if staticSessionManager == nil && domain != .empty {
let manager = SessionManager(serverTrustPolicyManager: ServerTrustPolicyManager(policies: getSecurityPolicies(certificate: SSLCertificate.getCertificate("certificateName")!)
))
staticSessionManager = manager
} else {
staticSessionManager = SessionManager.default
}Alamofire handles the pinning logic and makes integration easier.
Best Practices and Maintenance
- Monitor Certificate Expiry: Certificates expire and must be renewed in the app before they expire. Otherwise, it will lead to connectivity being lost by users.
- Handle Pinning Failures Gracefully: Provide polite error messages and alternative options if pinning validation fails.
- Plan for Certificate Rotation: Implement mechanisms, like pin sets or dynamic pin updates, to reduce disruption when certificates are updated.
- Combine with Other Security Measures: Implement SSL pinning along with secure storage, encrypted communication, and certificate transparency to guard against overall threats.
Pros and Cons of SSL Pinning
| Pros | Cons/Challenges |
| Strong protection against MITM and spoofing attacks | Increased development and maintenance complexity |
| Ensures the app only connects to legitimate servers | App updates required for certificate changes |
| Blocks unauthorized certificates, even from rogue CAs | Reduced agility for rapid server-side changes |
| Secures sensitive data in transit | Potential for service disruption if not managed properly |
| Hard for attackers to bypass or circumvent | Requires redundant pins to avoid a single point of failure |
Data Encryption Using CryptoKit
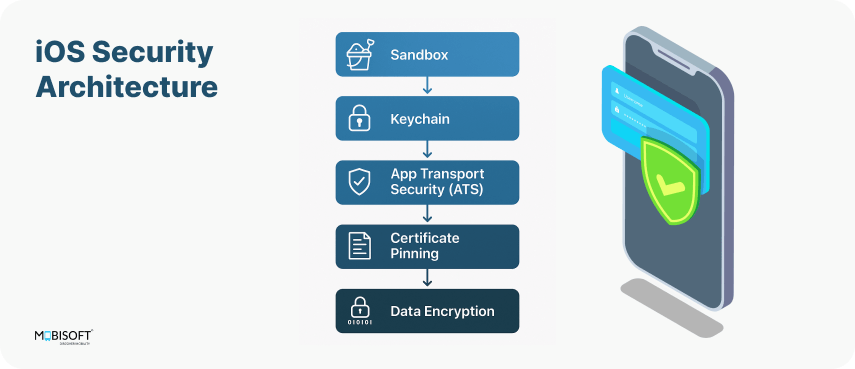
Why Encrypt Data in iOS Apps?
Protect Sensitive Information
iOS apps frequently process sensitive user information, including financial data, private communications, credentials, personal information, or private messages. Encryption guarantees that this information stays unreadable even if unauthorized parties gain access or intercept to it, reinforcing iOS app security.
Compliance with Regulations
Strong user data protections are needed under data protection laws such as GDPR and HIPAA. Compliance calls for a fundamental need for encryption and aligns with iOS app security best practices.
Mitigate Data Breach Impact
Encrypted data cannot be readily used in the event of device theft, malware, or unwanted access, therefore lowering the chance of data leaks and reputational damage, supporting overall mobile app security
Leverage Apple’s Hardware Security
When feasible, CryptoKit offers hardware-backed key storage and cryptographic capabilities for improved security, utilizing Apple's secure hardware (including the Secure Enclave).
What is CryptoKit?
CryptoKit is Apple’s high-level cryptography framework introduced in iOS 13. Abstracting complicated cryptographic specifics and using secure hardware as feasible, it offers easy-to-use APIs for hashing, encryption, decryption, key management, and digital signatures. It supports effective iOS app security testing.
Basic Steps to Encrypt and Decrypt Data with CryptoKit
Encrypt Data
Import CryptoKit
import CryptoKitGenerate a Symmetric Key
let key = SymmetricKey(size: .bits256)Encrypt Data Using AES-GCM
let message = "Sensitive information".data(using: .utf8)!
do {
let sealedBox = try AES.GCM.seal(message, using: key)
let ciphertext = sealedBox.ciphertext
let nonce = sealedBox.nonce
let tag = sealedBox.tag
// Store ciphertext, nonce, and tag securely
} catch {
print("Encryption failed: \(error)")
}AES-GCM is a modern, authenticated encryption algorithm supported by CryptoKit, providing both confidentiality and integrity and contributing to mobile app security best practices.
Decrypt Data
do {
let sealedBoxToOpen = try AES.GCM.SealedBox(nonce: nonce, ciphertext: ciphertext, tag: tag)
let decryptedData = try AES.GCM.open(sealedBoxToOpen, using: key)
let decryptedMessage = String(data: decryptedData, encoding: .utf8)
} catch {
print("Decryption failed: \(error)")
}Store Keys Securely
- Never place keys directly within your application.
- For the utmost security, keep encryption keys in the iOS Keychain.
Best Practices for Using CryptoKit
- Use Secure Key Storage: Always store keys in the Keychain, not in plain files or user defaults.
- Rotate Keys Regularly: Implement key rotation policies for long-term data protection.
- Handle Errors Gracefully: Always check for errors during encryption and decryption.
- Combine with Other Protections: Use encryption alongside secure networking (HTTPS), Keychain storage, and proper authentication.
Pros and Cons of CryptoKit Data Encryption
| Pros | Cons |
| Simple, modern Swift API, no need for low-level cryptography knowledge | Only available on iOS 13+ |
| Hardware-backed security when available | Requires careful key management, lost keys mean lost data |
| Supports strong, industry-standard algorithms | Not suitable for encrypting extremely large files (best for small to medium data) |
| Reduces risk of data breaches and regulatory penalties |
Managing secure data storage is critical to user protection. A mobile app development company can help implement Keychain access, encryption, and iCloud sync securely.
Input Validation and Sanitization
Input validation and sanitization are fundamental security practices in iOS app development, serving as the first line of defense against a wide range of attacks, including injection (SQL, XSS), buffer overflows, and data corruption. Here’s a detailed explanation of why and how to use these techniques effectively:
Why Use Input Validation and Sanitization in iOS Apps?
Prevent Injection Attacks
Without validation, attackers can inject malicious data (such as SQL commands or scripts) that compromise your app’s data and logic.
Protect Against Buffer Overflows
Unchecked input lengths can lead to memory corruption and security vulnerabilities.
Maintain Data Integrity
Ensures that only properly formatted, expected data is processed and stored, reducing bugs and logic errors.
Comply with Security Standards
Regulatory frameworks and best practices (like those from OWASP) require robust input validation to protect user data and app integrity.
Prevent Unauthorized Access
Checking deep link parameters and user input will help you prevent attackers from circumventing authentication or gaining prohibited areas of your app.
How to Use Input Validation and Sanitization in iOS
Validate All User Inputs
Use Regular Expressions
Define strict patterns for expected input (e.g., email, phone number, username), which is a part of secure coding for mobile apps.
let input = "user@example.com"
let emailRegex = "^[A-Z0-9a-z._%+-]+@[A-Za-z0-9.-]+\\.[A-Za-z]{2,}$"
let isValid = NSPredicate(format:"SELF MATCHES %@", emailRegex).evaluate(with: input)
if isValid {
// Safe to proceed
} else {
// Reject or prompt user
}This ensures only correctly formatted emails are accepted, improving iOS app security.
Type and Length Checks
Make sure the data matches the expected type and is within the allowed length.
let username = "john_doe"
if username.count >= 3 && username.count <= 20 {
// Valid length
}Allowlist (Whitelist) Validation
Define exactly what is allowed, rather than trying to block known bad inputs.
let allowedRoles = ["admin", "user", "guest"]
if allowedRoles.contains(inputRole) {
// Valid role
}Allowlisting is more secure than deny listing, which can be bypassed by attackers.
Sanitize Inputs
Remove or Encode Dangerous Characters
Strip or encode characters that could be used in injection attacks (e.g., <, >, ', ").
// Example: Encode HTML special characters to prevent XSS
let sanitizedInput = input.replacingOccurrences(of: "<", with: "<")
.replacingOccurrences(of: ">", with: ">")Validate Deep Link Parameters
Always check and sanitize parameters from deep links to prevent unauthorized access or injection.
Frameworks and Tools
- Use NSRegularExpression for complex pattern matching in Swift.
- For user-generated content, always encode output before rendering in web views or UI.
Pros and Cons of Input Validation and Sanitization
| Pros | Cons |
| Blocks a wide range of attacks (SQLi, XSS, buffer overflow) | Can be overly restrictive if not designed carefully, potentially impacting user experience |
| Improves app stability and data integrity | Requires ongoing maintenance as app features evolve |
| Required for compliance with security standards |
Runtime Protection with Jailbreak Detection
Why Use Runtime Protection and Jailbreak Detection?
Prevent Reverse Engineering and Tampering
Jailbroken devices bypass security measures already present in iOS to enable attackers access to app insides, code modification, and protection circumvention. This makes sensitive information and intellectual property available for misuse or theft, highlighting the need for jailbreak detection in iOS apps.
Block Malicious Runtime Attacks
Attackers can insert harmful code, connect app methods, or use debugging tools on a jailbroken device to modify app behavior live. This could result in privilege escalation, unauthorized access, or certificate theft.
Preserve App Integrity and Brand Reputation
By ensuring your app runs only in safe environments, runtime protection, including jailbreak detection, guards against consumers and preserves your app's image.
Meet Compliance and Regulatory Requirements
Many industry requirements ask programs, especially in finance, healthcare, and business situations, to actively guard against tampering and unauthorized access.
How to Use Runtime Protection and Jailbreak Detection
Jailbreak Detection
Jailbreak detection involves checking for signs that the device’s security model has been compromised. Common techniques include
Checking for Known Jailbreak Files/Paths
func isJailbroken() -> Bool {
let jailbreakPaths = [
"/Applications/Cydia.app",
"/Library/MobileSubstrate/MobileSubstrate.dylib",
"/bin/bash",
"/usr/sbin/sshd",
"/etc/apt"
]
for path in jailbreakPaths {
if FileManager.default.fileExists(atPath: path) {
return true
}
}
return false
}Testing Write Access Outside the Sandbox
func canWriteOutsideSandbox() -> Bool {
let testPath = "/private/jailbreakTest.txt"
do {
try "test".write(toFile: testPath, atomically: true, encoding: .utf8)
// Clean up
try FileManager.default.removeItem(atPath: testPath)
return true
} catch {
return false
}
}Detecting Suspicious Dynamic Libraries
func hasSuspiciousDyld() -> Bool {
for i in 0..<_dyld_image_count() {
if let name = _dyld_get_image_name(i),
String(cString: name).contains("MobileSubstrate") {
return true
}
}
return false
}Best Practice: Combine multiple checks for higher reliability, as sophisticated jailbreaks may try to hide their traces.
Runtime Application Self-Protection (RASP)
RASP is a broader concept that includes:
Detecting Debuggers at Runtime
func isDebuggerAttached() -> Bool {
return getppid() != 1
}Monitoring for Code Injection and Hooking
Use third-party SDKs (e.g., Arxan, Appdome, Guardsquare iXGuard) to automate runtime integrity checks, obfuscate critical logic, and block known attack vectors.
Real-Time Threat Monitoring
Log suspicious activity, restrict app functionality, or terminate the app if a threat is detected.
Responding to Threats
- Restrict or Disable Sensitive Features: If a jailbreak or tampering is detected, limit access to sensitive data or features.
- Alert the User or Security Team: Optionally notify users or send logs for further analysis.
- Terminate the App: In high-risk scenarios, force the app to close to prevent further exploitation.
Pros and Cons
| Pros | Cons |
| Raises the barrier for attackers, making exploitation and reverse engineering much harder. | Can be bypassed by advanced attackers (no method is 100% foolproof). |
| Protects sensitive data, intellectual property, and user trust. | May cause false positives, affecting legitimate users (e.g., enterprise devices with custom profiles). |
| Helps meet compliance requirements in regulated industries. | Requires ongoing updates to keep up with new jailbreak techniques. |
Secure Memory Handling
Why Use Secure Memory Handling?
Protect Sensitive Data in RAM
Sensitive data like passwords, authentication tokens, cryptographic keys, or personal user information may be kept in memory while an app is running. This data may be exposed via memory dumps, debugging, or exploitation of memory weaknesses if not appropriately handled. Secure memory handling in iOS mobile app security mitigates such risks effectively.
Prevent Memory-Based Attacks
Attackers can get or modify sensitive data by means of memory leaks, buffer overflows, or retention cycles. Safe memory management lowers the risk of such attacks by ensuring sensitive data is not left lingering in memory longer than is needed.
Meet Security and Compliance Requirements
Many security standards and guidelines call for sensitive data to be securely managed in memory to prevent unauthorized access, as well as encrypted while in motion or at rest. These principles are central to mobile app security best practices.
Avoid Memory Leaks and Performance Issues
Good memory management makes your app less vulnerable to crashes or resource depletion and keeps it running efficiently, therefore reducing the chance of leaks and performance slowdown.
How to Use Secure Memory Handling in iOS
Use Automatic Reference Counting (ARC) and Safe Data Types
- ARC automatically manages object lifecycles and releases memory when objects are no longer referenced to stop leaks and dangling pointers.
- Especially in closures and delegate patterns, always use weak and strong references correctly so as not to cause retained cycles.
Minimize Sensitive Data Exposure in Memory
- Clear sensitive data from memory as soon as it’s no longer needed.
For example, after using a password or token, overwrite the variable and set it to nil:
var password: String? = "UserSecret123"
// Use password for authentication
password = nil // Clear from memory- For data buffers, zero out the memory before releasing:
var sensitiveData = Data("secret".utf8)
sensitiveData.resetBytes(in: 0..<sensitiveData.count)
sensitiveData = Data()Avoid Unsafe Memory Operations
- Unless very necessary, steer clear of explicit memory allocation or unsafe pointers. Unsafe memory operations can lead to vulnerabilities, including buffer overflows and leaks.
- Always perform bounds checking and validate input when working with data buffers.
Store Long-Lived Secrets in Secure Storage
- Shun retains sensitive data such as passwords or keys in memory for longer than necessary. Store secrets securely for the long term using the iOS Keychain or Secure Enclave, which is critical for iOS app security.
Use Secure Enclave for Cryptographic Keys
- For cryptographic operations, take advantage of the Secure Enclave, which performs operations in a hardware-protected environment, never exposing keys to app memory.
Profile and Monitor Memory Usage
- Use Instruments from Xcode along with the memory graph debugger to profile your app, identify leaks, and ensure that sensitive information is not in memory.
- Test under different conditions of memory and devices to reliably perform consistently.
Pros and Cons of Secure Memory Handling
| Pros | Cons |
| Protects sensitive data from memory scraping and runtime attacks. | Requires careful coding and awareness of object lifecycles. |
| Reduces the risk of memory leaks, crashes, and performance issues. | May add minor performance overhead if frequently zeroing memory or using secure APIs. |
| Helps meet compliance and security best practices. | Secure Enclave usage is limited to supported devices and specific use cases. |
| Enhances overall app stability and user trust. |
Security Practices Comparison
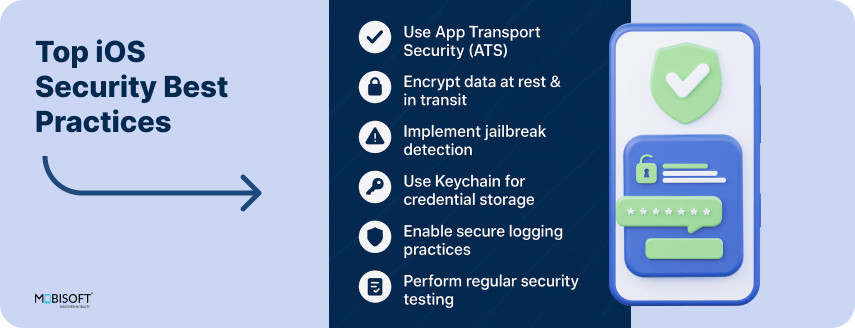
Being a flagship in our digital life, iOS apps have to be secured unconditionally. The growing threat landscape including data breaches, reverse engineering, and much more sophisticated attacks on a network, calls for a higher grade of approach towards the app's security. In conjunction with secure coding practice, developers have a host of best practices they can put in place to protect an application: vigorous data encryption, biometric authentication, SSL pinning, input validation, jailbreak detection, and secure memory handling, to name a few. The more of these developers that can be incorporated, the less will be left for an attacker to exploit, and this will safeguard the user's data concerning the developer's brand reputation.
Building on Apple's built-in security frameworks, with the security of the app being extended to the prudent update of dependencies, strengthens in turn the defense of the app against threats being wrought. In the long run, though, a secure iOS app meets all regulatory compliance standards, and more importantly, it has created a trust factor amongst users that revenue into long-term success in the markets.
| Practice | Security Impact | Implementation Complexity | Risk Mitigation |
| Keychain Storage | High | Medium | Data at rest |
| Biometric Auth | High | Low | Unauthorized access |
| SSL Pinning | Critical | High | MitM attacks |
| Data Encryption | High | Medium | Data breaches |
| Input Validation | Medium | Low | Injection attacks |
| Jailbreak Detection | Medium | Low | Reverse engineering |
| Secure Memory Handling | Low | Low | Memory exploits |
iOS developers may create applications that are resistant, dependable, and in accordance with the highest mobile security standards by regularly implementing these safety precautions.
Conclusion
Prioritize these practices based on your app’s risk profile:
- Important applications (e.g., financing): Enforce SSL pinning, biometrics, and Keychain.
- Combine CryptoKit encryption with jailbreak detection in data-sensitive apps.
- Require HTTPS, input validation, and memory sanitization for all apps.
Regular audits and dependency updates are non-negotiable for maintaining security. Tools like OWASP ZAP and automated SAST/DAST scans should complement these practices to catch evolving threats.
Final Tip
Over personalized solutions, always employ Apple's built-in security tools like Keychain, CryptoKit, and LocalAuthentication; they are battle-tested and gain from hardware-level security.



 July 4, 2025
July 4, 2025


