Adoption of cloud computing has moved from being an option to being central to how organizations deliver applications and services. As businesses scale in the cloud, the need to integrate AWS security best practices at every phase of development has reached an unprecedented level. This practice, known as DevSecOps, combines development, operations, and security in one streamlined, continuous workflow.
Agencies that use continuous security assessment and automated scanning reduce high- and critical-vulnerability dwell time by 88% compared to manual scanning baselines. The U.S. Department of Defense cites integration of AWS security tools such as Amazon Inspector as “central to rapid risk reduction in cloud-native and hybrid defense systems.”
In today’s environment, research shows that a majority of cloud workloads have delayed threat detection and configuration errors. These weaknesses often lead to costly breaches. Amazon Inspector, for example, is not just a convenient feature but a strategic enabler. It helps organizations apply DevSecOps best practices and enforce enterprise-wide cloud security in DevSecOps without slowing down software development cycles.
Learn more about how our cloud development services can help you build secure, scalable applications in AWS.
What is an Amazon Inspector?
Amazon Inspector uses AI to help safely manage AWS cloud security operations. This helps it inspect AWS Lambda security for threats and errors. While scans occasionally occur manually or ad hoc, Inspector scans in real time, aiding teams in preventing difficulties before production runs.
The inspector maintains compliance with guidelines like CIS Benchmarks, PCI DSS, and NIST, with proof of regular security assessment automation being performed. It translates tough security data into easy, comprehensible insights. This greatly helps in supporting rapid responses, management of threats, risk mitigation in AWS, and embedding security in the DevSecOps pipeline.
To further strengthen this, many enterprises integrate penetration testing services to validate vulnerabilities and enhance Inspector’s automated scanning.

Key Features of Amazon Inspector
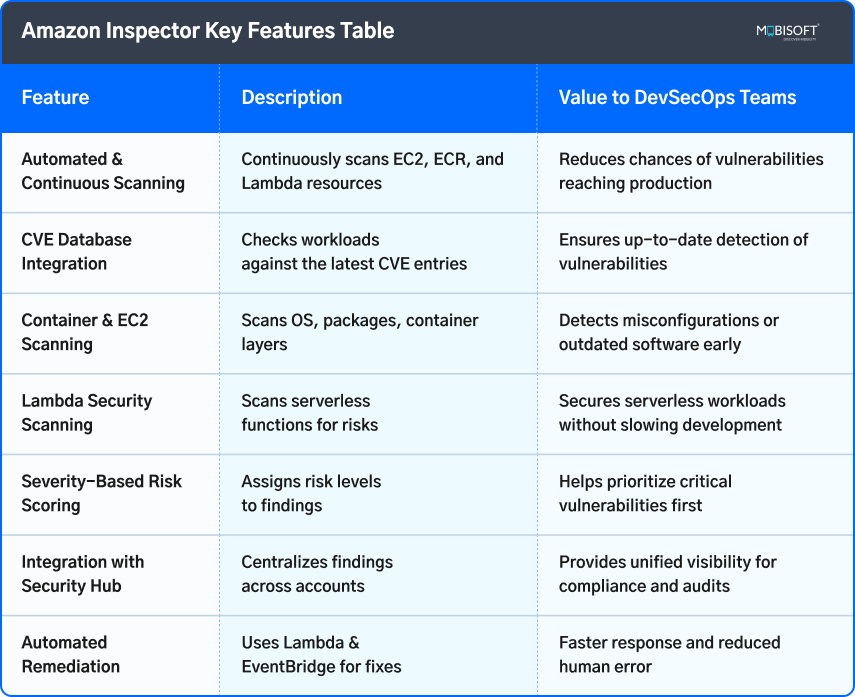
Automated and Continuous Scanning
Along with Lambda functions, Amazon Inspector also scans the ECR for container images and EC2 servers. This cloud vulnerability scanning at every step of deployment and management ensures complete security. It further lowers the possibility of an exploited vulnerability ever reaching production. Responses and lower odds that an exploited vulnerability ever reaches production.
CVE Database Integration
The Inspector operates in conjunction with AWS security feeds and outside Common Vulnerabilities and Exposures (CVE) databases to remain current. When a new vulnerability is published in the CVE database, Inspector promptly assesses resources in relation to it. For instance, if a container image contains a package with a newly identified exploit, Inspector flags it ahead of deployment, improving vulnerability management in AWS.
Container and EC2 Scanning
The inspector also covers Amazon EC2 instance scans and container image scans in ECR. EC2 analyzes operating systems, installed packages, and network setups, detecting misconfigurations or outdated software. In container applications, examining the layers is the first task. This enables teams to detect vulnerabilities early in the CI/CD pipeline. Finding vulnerabilities this early stops vulnerable containers from ever entering production and offers safer application delivery, especially in highly automated DevOps security pipelines.
Lambda Security Scanning
Serverless functions often bypass traditional security products due to their runtime on non-persistent server instances. It can detect risks like excessive permissions in IAM, insecure environment variables, or outdated library versions. This model, adopted by teams involved in microservice or event-driven architecture development, ensures serverless code is inherently secure and vulnerabilities are prevented from having their potential effect on other services or end-users. This aligns closely with security testing in AWS practices.
Severity-Based Risk Scoring
Every Inspector finding gets a severity score, allowing teams to focus on addressing issues. Critical vulnerabilities that may result in data breaches or privilege escalation are prioritized, while less severe issues are postponed for later attention. This stops teams from wasting resources in time and effort on minor alerts. It guarantees that high-risk issues get immediate attention, supporting DevSecOps automation tools adoption.
Integration with AWS Security Hub
Inspector seamlessly works with your AWS Security Hub to offer you a single dashboard for all your operations and data. With centralized reporting, the management can supervise every aspect of the organisation and its workings, down to multi-account set-ups, aligning with AWS DevSecOps best practices.
Automated Remediation and Notification
Inspector collaborates with AWS EventBridge and Lambda to invoke remediation workflows programmatically. As a case in point, upon identifying a high-severity vulnerability, AWS Lambda can invoke an automatic patch or disable an unsafe configuration programmatically. Notifications can also be pushed to teams via Security Hub or other communication systems, thereby ensuring rapid awareness. Security automation in AWS reduces human error, provides faster response times, and reinforces an entire organization's security posture.
Explore how DevOps security services can complement Amazon Inspector in building a secure development lifecycle.
Amazon Inspector Key Features Table
How Amazon Inspector Works
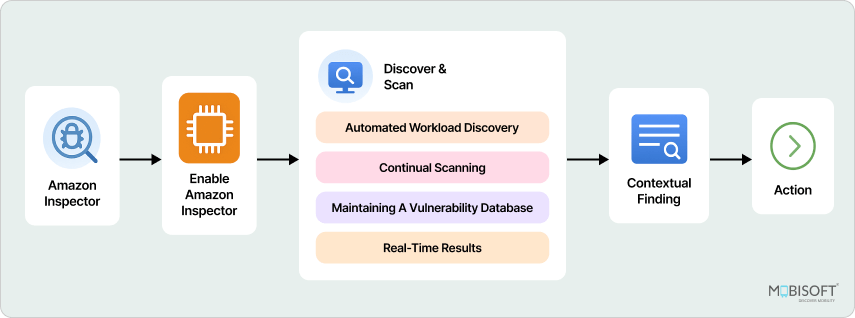
Resource Discovery
The first phase of Amazon Inspector consists of AWS resource discovery. Inspector automatically discovers EC2 instances, container images in ECR, and Lambda functions in your accounts. This feature abolishes manual inventorying, which is very handy in highly dynamic environments where resources keep being spun up or changed frequently. It ensures, as an added advantage, that AWS DevSecOps teams do not have any workload going uncovered. Transient resources set up at times of tests and staging are included as well, thus reducing blind spots and improving security coverage in general.
Continuous Scanning
When the Inspector discovers resources, it also starts continuous scanning. This isn't periodic snapshot scanning; it's continuous scanning, consistently updating as workloads, dependencies, and configurations change. When a developer launches a new container image or modifies a Lambda function, Inspector concurrently scans it for both recognized vulnerabilities and misconfigurations, ensuring infrastructure as code (IaC) security compliance.
Vulnerability Assessment and Risk Scoring
Inspector matches found resources to CVE databases and AWS security best practices to determine vulnerabilities. The findings receive a severity-based risk score, clearly indicating those vulnerabilities requiring remediation promptly. Top-of-list vulnerabilities, critical vulnerabilities such as exposed credentials or out-of-date software, have lower-priority vulnerabilities documented as watch items for monitoring purposes.
Notification and Alerts
Results are reported to appropriate teams by AWS Security Hub, EventBridge, or custom alert channels. This procedure provides security, managers, and developers with helpful notifications without having to individually review consoles. The notifications can contain information such as an affected resource, type of vulnerability, and correct steps to resolve it, and this can enable teams to act in an instant and orderly manner in line with DevSecOps best practices.
Automated Remediation
With the help of AWS Lambda and EventBridge, Inspector ensures continuous remediation. If an AWS Lambda function scans a discrepancy, for instance, it will automatically update the EC2 server or swap out the container. This demonstrates security assessment automation in practice.
Prioritization for DevSecOps Workflows
Inspector allows teams to integrate security with the CI/CD pipelines. With the help of discoveries and respective risk scores, the team can decide on selective remediation. This approach helps fix only the critical issues, and not hindering the development, supporting DevOps security workflows.
Check out our guide on CI/CD pipeline security in AWS to understand how Inspector enhances automated DevOps pipelines.
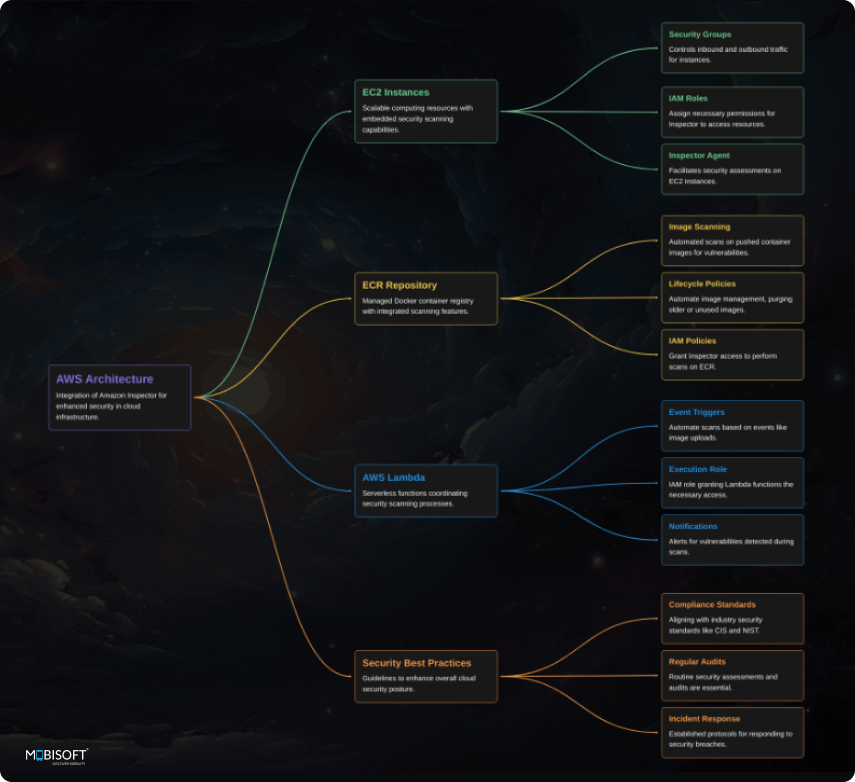
Supported AWS Services:
Amazon EC2 (Instance Scanning)
Inspector scans for vulnerabilities in EC2 instances, outdated software, and improper configurations. This helps keep instances safe and reduces the likelihood of compromise through your AWS cloud security infrastructure.
Amazon ECR (Container Image Scanning)
For container workloads, Inspector scans containers in ECR stores. It detects vulnerable layers and out-of-date dependencies, and prevents insecure containers from being sent to production. This improves cloud vulnerability scanning efficiency.
AWS Lambda (Serverless Security Analysis)
Inspector scans AWS Lambda serverless functions for potential threats like overpermissions, insecure environment variables, and outdated libraries. This maintains Lambda security and compliance without slowing down development.
Setting Up Amazon Inspector for DevSecOps
Step 1: Enable Amazon Inspector
- Activate it by logging on to the AWS Console, going to Amazon Inspector, and clicking on "Enable." Relevant permissions allow for smooth scanning without losing resource security.
- Double-check all relevant AWS accounts are included, especially if you're utilizing multiple accounts in AWS Organizations. Missing accounts can offer blind spots, and vulnerabilities remain unmitigated.
Step 2: Define Scan Scope
- Select to scan all resources automatically or just specific ones. Automatic scanning reduces the chance of misses in the workload, although you can do it in test phases as well as for sensitive systems.
- Scan critical workloads first, for example, production EC2 instances, containers holding customer-facing applications, etc. This ensures resources, which would have the greatest impact in case of compromise, face immediate responses.
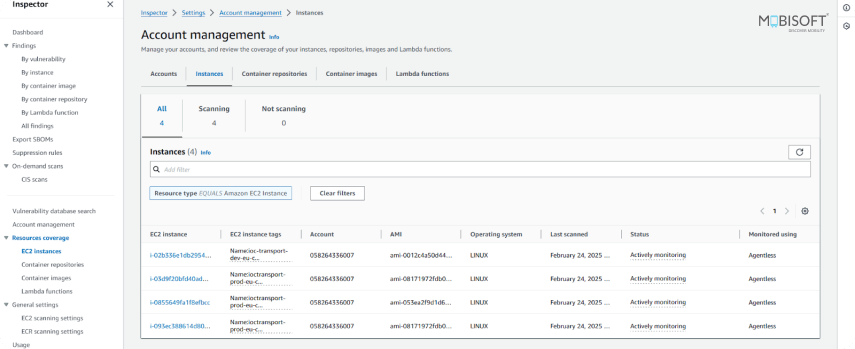
Step 3: Configure Notifications and Automation
- Use Amazon EventBridge to set up automated responses to recognized findings. Severity-critical vulnerabilities can trigger Lambda functions to patch, isolate, or log vulnerable resources.
- Integrate into AWS Security Hub to centralize alerts across accounts. These integrations support security automation in AWS and enable faster DevOps security responses.
Step 4: Monitor and Remediate Findings
- Scan consoles or dashboards to observe vulnerabilities. Every finding contains a recommended action and security score.
- Focusing on high-risk items first reduces breaches and supports remediation in time. Use Lambda or Systems Manager to automate patching for critical vulnerabilities, ensuring efficient vulnerability management in AWS.
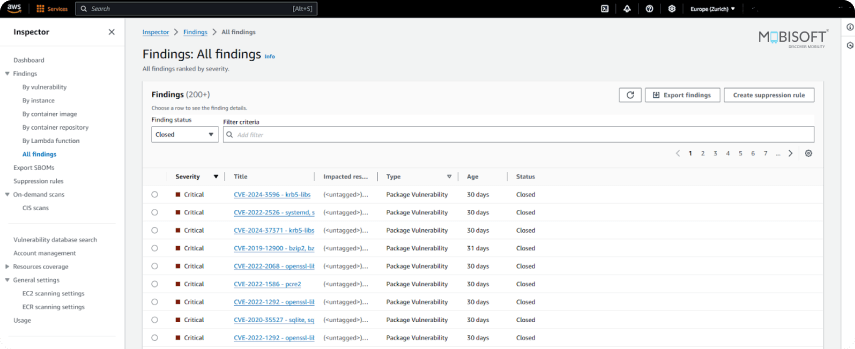
Step 5: Integrate into DevSecOps Pipelines
- Implement the Inspector before deployment. This will ensure all the new containers and Lambda functions are secure.
- Keep a constant check on the dashboards to learn threat detection in AWS and scan other anomalies that can hinder progress.
Learn how to improve your security posture with DevSecOps vulnerability mitigation strategies for proactive risk management.
Benefits of Using Amazon Inspector in DevSecOps
Shift-Left Security Approach
20% of breaches in 2025 started with the exploitation of software vulnerabilities, up from 12% in 2022. 74% of all breaches involved the cloud, either as initial access or impacted resource. Integrating Amazon Inspector into CI/CD pipelining reduces breaches and costly repairs in the future. This is because it detects anomalies so that the codes can run smoothly. The team can trust new releases to be scanned automatically for risks, and this also avoids delaying innovation without ever having to compromise safety. This is the foundation of DevSecOps best practices.
Automated Compliance and Risk Management
The inspector constantly assesses resources against industry-leading standards such as CIS, PCI DSS, and NIST. Results can be monitored in centralized dashboards, ensuring good audit trails exist. This decreases manual labor and aids governance needs in compliance-driven businesses. It also enables rapid evidence of compliance with regulations, while it automatically performs tedious checks using DevSecOps automation tools, which would otherwise take considerable time.
Enhanced Visibility and Prioritization
Inspections assign severity scores to findings, aiding teams in prioritizing high-risk vulnerabilities initially. It emphasizes this information to enable DevSecOps teams to use their time effectively, reducing effort loss and ensuring quick responses to urgent security issues. This strengthens risk mitigation in AWS strategies.
Seamless Integration with AWS Services
Inspector works in combination with AWS Lambda, Security Hub, EventBridge, and CloudWatch to create an integrated security system. It offers automatic reminders, fixing issues, and live monitoring. When security becomes part of an integral cloud workflow, teams can move quickly and guarantee everything keeps operating without any issues, needing less manual work. This is critical to cloud security in DevSecOps.
Proactive Risk Reduction
Regular checks and correction programs allow organizations to correct and contain risks early before they develop into problems. Early correction minimizes potential business loss and develops strong systems. In the long run, regular patterns emerge, and DevOps security practices can be optimized to prevent repeat problems from occurring.
Strengthen your DevSecOps pipelines with automated DevOps workflows that align with Amazon Inspector’s automation capabilities.
Best Practices for Using Amazon Inspector in DevSecOps
Enable Inspector Across All Accounts and Regions
- Ensure Amazon Inspector is enabled in all AWS accounts and regions being used by your enterprise.
- Using AWS Organizations can automate this, minimizing blind spots and ensuring all resources are accounted for.
Automate Remediation with AWS Lambda
- Set up Lambda functions to process high-severity findings without human interaction.
- This decreases response time, reduces human error, and keeps valuable resources protected without human interaction.
Integrate with CI/CD Pipelines
- Put Inspector in your build and deployment pipeline. Scan container image, EC2, and Lambda functions before they're executed in production.
- This enables you to discover vulnerabilities sooner and enable shift-left security practices.
Leverage EventBridge for Notifications
- Set up automated alerts for high-risk results.
- Event-driven alerts ensure security teams receive immediate notice.
Regularly Review Findings
- Occasionally, check results and trends using dashboards or Security Hub.
- This helps in identifying common issues, narrowing scans to be more specific, and continuous refinement of security practices.
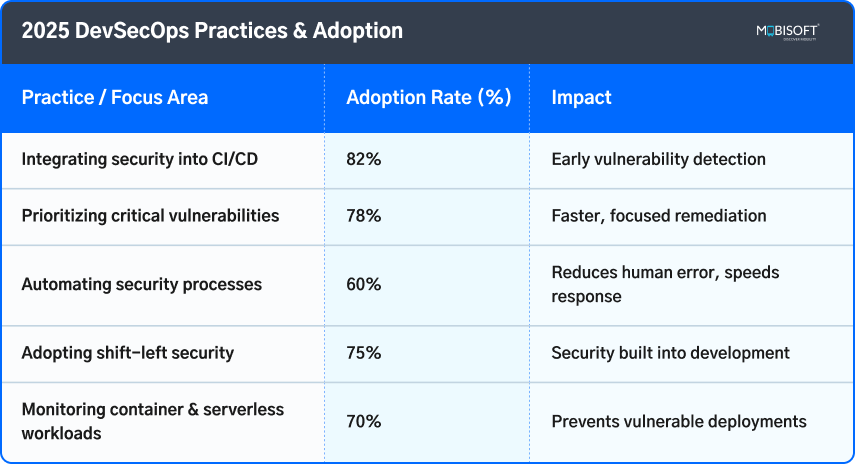
2025 DevSecOps Practices & Adoption
Conclusion
Amazon Inspector offers security to help manage risk in the cloud. Amazon Inspector regularly examines EC2 instances, container images, and Lambda functions to identify vulnerabilities in advance. Rather than after production systems, which is how standard security systems operate. This DevSecOps shift-left approach keeps security as a continuous central focus in software creation, rather than treating it as an afterthought. This allows teams to act swiftly while maintaining safety as the focus of their procedure.
They can stay updated on trends, identify frequent issues, and consistently modify security measures to align with a constantly evolving cloud technology. These functions provide reduced risk, enhanced governance, and improved business resilience within an agile cloud setting.
And last, by adopting Amazon Inspector, businesses can create securely constructed, compliant, and highly available applications while ensuring security in complete sync with today's AWS DevSecOps best practices.
Businesses can create securely constructed, compliant, and highly available applications while ensuring end-to-end protection with advanced cloud security services.
Key Takeaways:
- Introduction: The cloud needs security at each stage of development. DevSecOps integrates security into the workflow, and Amazon Inspector discovers problems early before a breach or compliance crisis.
- Continuous Scanning: The inspector continually inspects EC2 instances, container images, and Lambda functions to ensure new updates get examined for risk before production.
- Up-to-Date Threat Intelligence: Utilization of AWS and external CVE databases ensures Inspector receives up-to-date information regarding new vulnerabilities, flagging significant concerns immediately for expedited correction.
- Prioritised Risk Management: Discoveries are given risk scores, allowing devs to filter remediation based on priority. This helps waste less time.
- Automation and Integration: It offers continuous alerts, reporting, and remediation by integrating with Security Hub, EventBridge, and Lambda.
- Best Practices: Turn on Inspector for all regions and accounts, include it in CI/CD pipelines, and periodically check for results to improve security controls continually.
- Business Impact: Inspector makes security a real-time, interactive experience so organizations can develop secure, compliant, and resilient cloud apps without affecting development.



 September 26, 2025
September 26, 2025


