Cloud adoption is at the core of how businesses manage their workloads today. With its growth, AWS security monitoring is now imperative and non-negotiable, and has become a business imperative. Attackers annually discover new and sophisticated methods to exploit vulnerabilities in cloud infrastructures. This subjects sensitive information to risk as well as customer trust and regulatory alignment.
The service goes beyond simple observation. Amazon GuardDuty, a leading AWS cloud security service, utilizes AWS data logs and machine learning in AWS security, along with different cloud threat intelligence platforms. Its goal is to discover dangers potentially hidden from human detection. It aims to help organizations react preemptively before attackers gain control over accounts, move data, or freeze workloads.
Survey data shows that 56% of organizations operate in hybrid cloud setups, but only 42% have real-time proactive cloud threat detection for AWS workloads. Products like GuardDuty offer an avenue to address this detection gap. For companies, deployment of these tools is less about technology and more about reinforcing resilience in everyday procedures.
Businesses often combine such monitoring with cloud infrastructure consulting services to optimize their architecture and reduce vulnerabilities.
What is Amazon GuardDuty?
Amazon GuardDuty is a cloud threat detection AWS service for assisting entities in discovering threats before they escalate. Rather than being based on manual log examination or siloed monitoring tools, GuardDuty integrates AWS threat detection with an all-in-one platform. GuardDuty automatically monitors activities within AWS environments for compromised account signs, activities with unusual access behavior, and data-extraction efforts.
The value to enterprises with GuardDuty is its focus on turning raw data into actionable intelligence. Many security experts fail because it is not a lack of data with which they struggle, but too much information to sift through. GuardDuty properly takes raw logs and makes them actionable information prioritized by security teams to quickly act upon. In practice, this equates to teams wasting less time chasing dead ends and more time reacting to legitimate events.
For businesses, this specific role extends beyond mere detection of threats; instead, it represents an entirely exhaustive strategy, one whose intent is to minimize threats en masse, significantly supporting both AWS security best practices and compliance needs. To strengthen defenses further, organizations can also explore vulnerability assessment and penetration testing services.

Cloud Security Threat Landscape (2025)
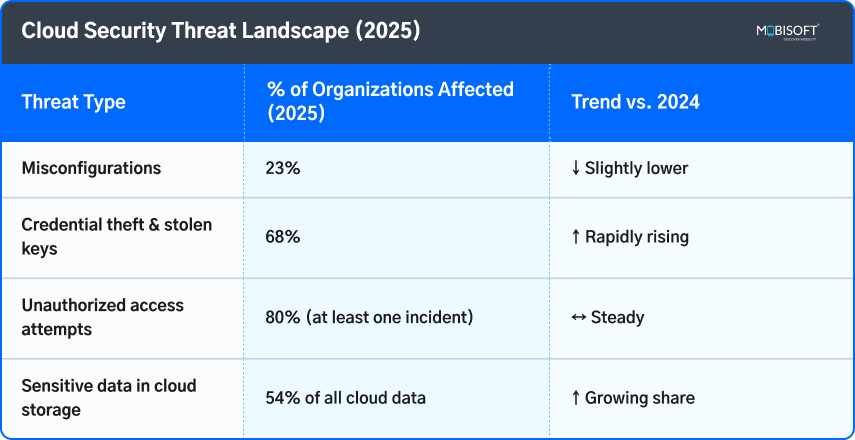
Companies combating these threats often combine GuardDuty insights with cloud cybersecurity services for AWS to create stronger, multi-layered defense mechanisms.
Key Features of Amazon GuardDuty
GuardDuty offers a range of Amazon GuardDuty features that make AWS security monitoring more practical and effective for businesses:
Continuous Threat Detection
GuardDuty is always running in the background to detect threats within AWS environments. This functionality lets organizations find threats, whether there are scheduled scans or log analyses done manually. It is extremely crucial for distributed and multi-account environments, where monitoring is frequently broken up, a key GuardDuty AWS use case.
Machine Learning-Based Analysis
The service utilizes behavioral analysis and machine learning in AWS security to identify uncommon activities. Instead of relying strictly upon known signatures, it learns typical patterns and focuses upon departures from normalities. This approach allows teams to discover hitherto unseen threats and insider threats that most static tools consistently miss.
Threat Intelligence Integration
GuardDuty bolsters both accuracy and capability significantly by harnessing threat intelligence not just drawn from AWS itself, but also from an array of credible third-party entities that have expertise in cybersecurity. This diverse set of data streams enables the system to effectively recognize attempts to initiate communications with established malicious IP addresses, different sorts of botnets, or other questionable domains potentially harmful to it. Consequently, this development provides teams with enhanced outcomes while alleviating the necessity of managing their own data feeds.
Multi-Account Support
With AWS Organizations, GuardDuty has multi-account central visibility. Security managers can obtain an entire panorama of all activities and configurations at one central dashboard, rather than having to individually set up every single account by hand. This feature is most critical and useful in large-scale business establishments, as it is in distributed work teams based in different locations, demonstrating practical AWS GuardDuty tutorial use.
Automated Remediation
Outputs from GuardDuty can be sent to any number of services, for example, AWS Security Hub, Lambda, or Systems Manager, which can allow for automation of remediation steps. By establishing an end-to-end flow between detection procedures and subsequent remediation actions, organizations can reduce their incident response time and reduce the chance of incurring potential losses.
Scalable and Cost-Effective
Because GuardDuty is a managed service offering, there is no need to acquire and maintain further infrastructure by organizations. GuardDuty pricing is consumption-based, ensuring cost efficiency with scalability for enterprises of all sizes.
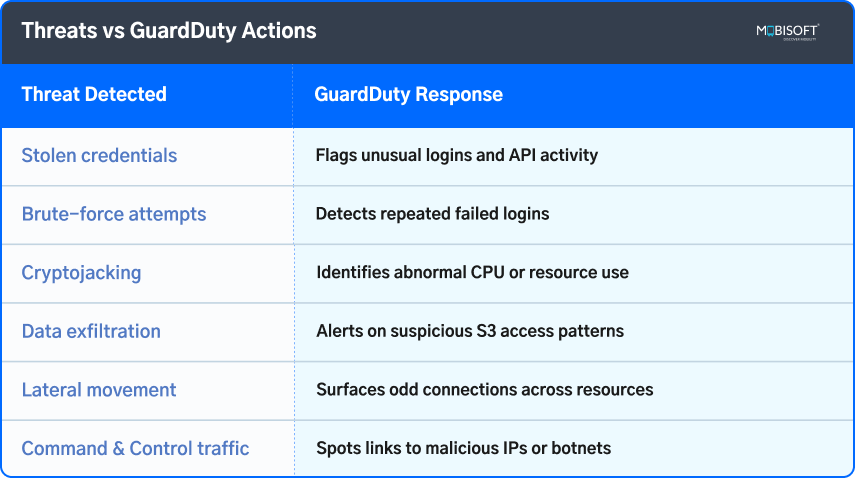
Threats vs GuardDuty Actions
How Amazon GuardDuty Works
The process is designed to be simple for customers, but here’s what goes behind the scenes:
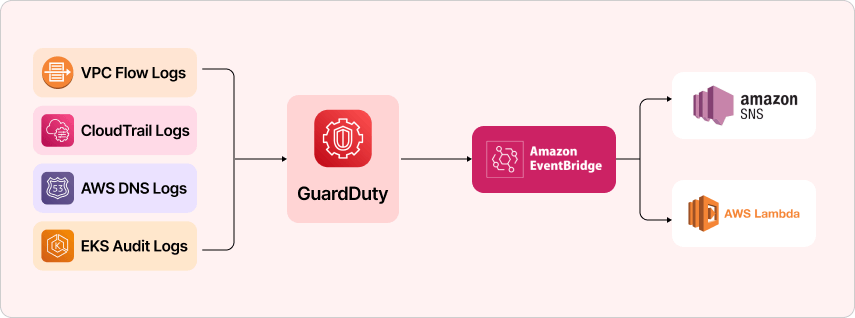
Log Data Collection
Amazon GuardDuty collects various types of logs containing records of activities within the AWS environment for AWS security monitoring.
- CloudTrail logs record API calls and offer information on how AWS services are accessed by administrators and end-users.
- VPC Flow Logs provide in-depth information on network traffic, enabling you to detect unexpected connections.
- DNS query logs also keep track of attempts to access domain names, showing attempts to access malicious sites.
Threat Analysis & Detection
The service applies behavioral analysis, statistical models, and machine learning in AWS security to spot unusual behavior. At the same time, it uses cloud threat intelligence platforms from AWS and partners to check for connections to known malicious hosts, strengthening AWS threat detection.
Security Findings & Alerts
As soon as GuardDuty detects unusual behavior, it creates a security finding. A finding contains information regarding an event and also has a severity level. The level can be low, medium, or high. These alerts can be used to enforce AWS security best practices.
Incident Response & Remediation
Finds can be integrated into AWS Security Hub, CloudWatch, or third-party SIEM systems. They can also trigger automatic workflows through Lambda or Systems Manager, supporting faster remediation. This allows organizations to move from detection to response without delays, showcasing GuardDuty’s role in advanced threat detection in AWS environments.
For backend teams, Amazon GuardDuty also works alongside essential AWS services for backend developers to create a more secure foundation.
Common Threats Detected by GuardDuty
Threats often start small, but can quickly escalate if not detected in time. Below are common GuardDuty AWS use cases to watch for:
Unauthorized Access & Account Compromise
- Nearly 30% of incident response cases in 2024 involved cloud environments.
- Overly permissive access and poor identity management contributed to 41% of incidents, as per reports.
- This can occur as a result of attackers who access through leaked credentials or stolen API keys.
- GuardDuty identifies suspicious API calls, login attempts coming through unintended regions, or access through disabled accounts.
Brute Force Attacks
- GuardDuty is capable of detecting a series of repeated failed login attempts, which frequently indicate the presence of brute force activity.
- These seemingly minor tests are very harmful. Often results in a complete takeover of the account if action is not taken promptly to stop them.
Malware & Cryptojacking
- GuardDuty, as part of AWS cloud security services, systematically discovers any anomalous resource consumption or behaviors.
- As it does this, it avoids potential financial loss due to lost computing cycles.
- Also averting the danger of being swept up in broader-based malware campaigns to do still more harm.
Data Exfiltration
- Amazon GuardDuty can identify and detect any suspicious access attempt to S3 buckets or data transfers not in accordance with normal, regular patterns of activity.
- The detection of such unusual behavior at an initial phase helps organizations take proactive steps to safeguard against breaches.
- This supports AWS security compliance by preventing sensitive information from escaping the protected sphere.
Network Intrusions & Lateral Movement
- Once an attacker gets into a network, they often resort to stealthy exploration of the system to learn more.
- Amazon GuardDuty can do an excellent job of calling out any unusual communication taking place between different AWS resources.
- Such unusual communications may also indicate lateral movement within user accounts.
Command and Control (C2) Activity
- Finally, GuardDuty continuously scans for any traffic sent out towards known malicious IP addresses or established botnets.
- These indicators often serve as clear evidence that a resource has been compromised.
- This is usually determined when the resource is found communicating externally with control servers used by attackers.
If your workloads include application load balancers, you can further strengthen visibility by processing AWS ALB logs with GoAccess.
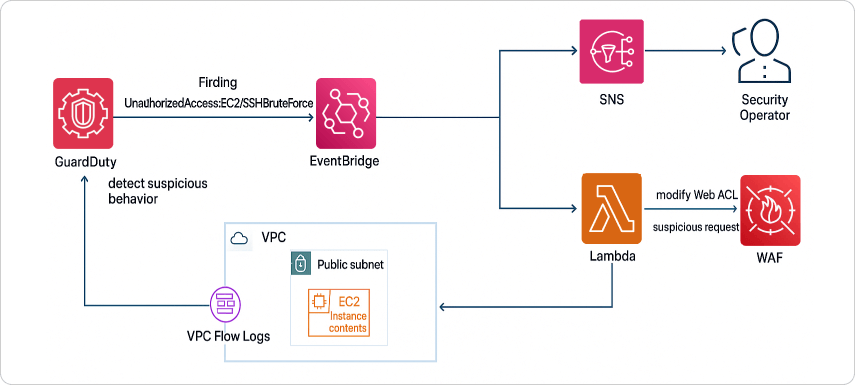
Setting Up Amazon GuardDuty
Enabling GuardDuty in AWS is a simple, one-click process that requires minimal configuration. Follow these steps to set up GuardDuty:
Enable GuardDuty
- Sign in to the AWS Management Console and open GuardDuty.
- Click on “Enable GuardDuty” to activate monitoring.
- The service starts reviewing activity across accounts and regions immediately, with no extra setup needed.
Configure Findings & Notifications
- Decide how findings should reach your security teams.
- Integrate GuardDuty with AWS Security Hub, AWS CloudWatch security alerts, or Amazon SNS
- This ensures high-severity warnings are delivered on time and through the right channels.
Analyze Findings regularly
- Use the GuardDuty console or connected dashboards to review alerts.
- Classify findings by severity and prioritize the ones that need urgent action.
- This step keeps teams focused and avoids missed risks.
Automate Threat Response
- Integrate GuardDuty with AWS Lambda or Systems Manager.
- Set up automated scripts to contain or remediate threats.
- Automating this step reduces delays and supports faster recovery.
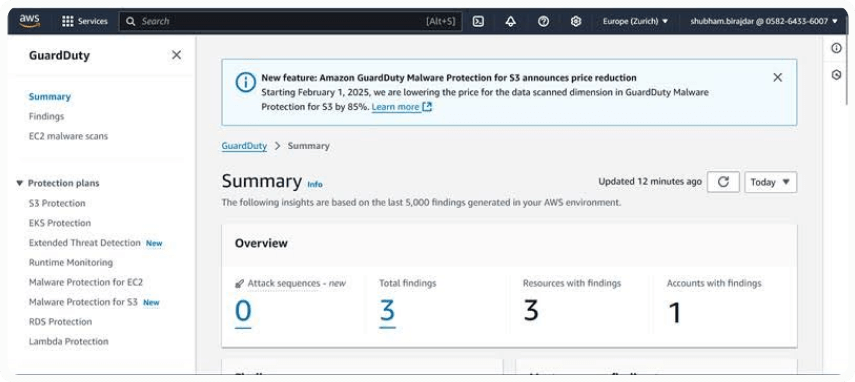
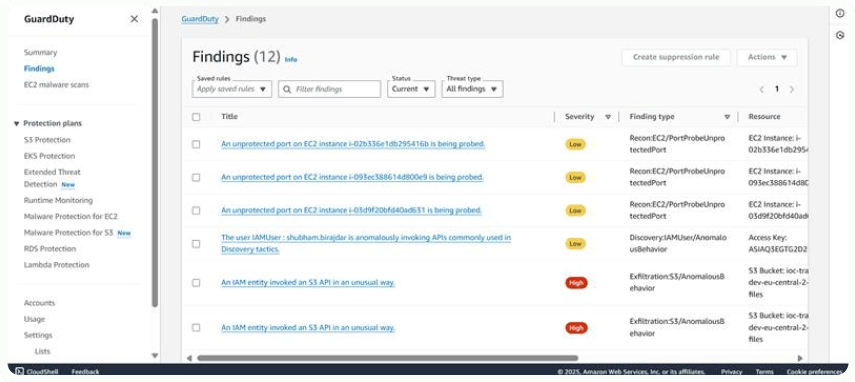
Check the findings
As part of deployment strategies, IT teams often configure AWS site-to-site VPN setup with FortiGate for secure connectivity between cloud and on-premises systems.
Best Practices for Using GuardDuty
To maximize Amazon GuardDuty’s effectiveness, follow these best practices:
Enable GuardDuty across all AWS accounts
GuardDuty should be turned on across every AWS account in your organization. Using AWS Organizations makes this process centralized and consistent, supporting AWS security monitoring at scale.
Automate threat response
AWS Lambda, being a cloud service, is much more susceptible to cyber attacks. GuardDuty integration with it allows you to automate responses to such attacks, enabling immediate reaction and minimizing human errors a key advanced threat detection AWS capability.
Regularly review findings
Use AWS Security Hub and connected dashboards to observe GuardDuty notifications across devices. This greatly helps sort activity on a priority basis and even learn threat patterns, reinforcing AWS security best practices.
Integrate with SIEM solutions
Implementing this allows your team to see not only cloud threats but also how they relate to overall security, improving both detection accuracy and response time, a practical guard duty use case.
Fine-tune detection rules
You can set filters for classifying alerts. This reduces the number of false positives, making the product more efficient for threat detection for AWS workloads.
Benefits of Using Amazon GuardDuty
Organizations benefit from GuardDuty in several ways:
Enhanced Security Posture
GuardDuty improves security resilience by continuously monitoring AWS environments. Its machine learning in AWS security models and cloud threat intelligence platforms makes it possible to detect threats in near real time.
Reduced Security Overhead
Teams don’t need to manually parse logs, since GuardDuty is automatically managed. Thus, the team can focus on priority tasks, making the process smoother and more affordable, a benefit of AWS cloud security services.
Faster Threat Response
GuardDuty integrates seamlessly with AWS services like Security Hub, Lambda, and Systems Manager. This connection enables automated responses to suspicious activity, supporting advanced threat detection on AWS.
Compliance & Governance
GuardDuty findings support compliance frameworks such as PCI DSS, GDPR, and HIPAA by providing evidence of continuous monitoring. Having clear audit trails and prioritized findings simplifies reporting and reinforces governance efforts, demonstrating AWS security compliance.
Conclusion
The UK’s 2025 Cyber Security Breaches Survey reports increasing cyberattack sophistication and highlights cloud security as a top priority area for defenses. Amazon GuardDuty provides a comprehensive solution by adding security to workloads running inside the AWS environment. It combines artificial intelligence, anomaly detection, and intelligence feeds to discover threats often left unnoticed in complex environments, fulfilling AWS threat detection needs.
GuardDuty is wider than simply addressing threat detection. It enables organizations to enhance governance overall and achieve levels of compliance by providing clear data for monitoring and easily accessible reporting assistance. For those companies working in competitive landscapes, these elements help retain confidence and minimize the risks of expensive interruptions.
In a cloud-first environment with threats that change by the day, GuardDuty provides organizations with a proactive defense and continued resilience to possible breach attacks, making it a key cloud security detection tool in AWS cloud security architecture.
To learn how to align GuardDuty with your business goals, explore our AWS cloud support and maintenance services.
Key Takeaways:
- Cloud security is not optional: As more workloads shift to AWS, businesses can't afford blind spots that endanger data, trust, and compliance.
- GuardDuty Analyses Data: instead of drowning teams in raw, unprocessed logs, it highlights critical threats, thus enabling quicker response times.
- Always-on monitoring fosters trust: Real-time detection removes dependence upon occasional checks or disjointed tools, creating blind spots.
- Machine learning refines detection: Learning normal behavior, GuardDuty discovers insider threats and new attacks in time to stop them.
- Threat intelligence increases accuracy: With AWS and reputable third-party feeds, GuardDuty can identify associations with known bad actors and minimize false notifications.
- Enhanced centralized visibility: Supporting multiple accounts causes managers to see the broader picture throughout distributed areas and teams.
- Automation decreases response time: Outputs of GuardDuty can trigger prebuilt workflows, and threats can be isolated before they cause extensive damage.
- Scalability keeps budget in check: As it's a managed service, GuardDuty scales to keep pace with expanding demands without new infrastructure or substantial upfront expenditures.
- Detection covers the actual threats: GuardDuty addresses threats to which most cloud infrastructure businesses have been most vulnerable, from stolen passwords to data theft and cryptojacking.
- Setup is quick and effortless: Enablement is one click, and integration into alerting systems ensures security teams never miss what matters.
- Best practices make the difference: Consistent rollout, alert tuning, SIEM integration, and regular reviews turn GuardDuty from a tool into a strategy.
- Benefits go beyond detection: they reduce operational strain, accelerate time to response, enhance compliance, and fortify governance.



 September 25, 2025
September 25, 2025


