In today’s technology-driven world, connecting your office network securely to cloud resources is essential. AWS Site-to-Site VPN makes this easy by creating encrypted connections, ensuring your data stays safe while traveling between your systems and Amazon’s Virtual Private Cloud (VPC). AWS Site-to-Site VPN enables secure connections between your on-premises network and AWS Virtual Private Cloud (VPC), allowing secure communication between local networks and AWS resources using IPsec tunnels for secure data transmission.
In this guide, we will learn the configuration of a site-to-site VPN connection from a local FortiGate firewall setup AWS to an AWS VPC via IPsec with static routing. Instances that you launch into an AWS VPC can communicate with your own remote network via a site-to-site VPN between your on-premise FortiGate and AWS VPC VPN. You can enable access to your remote network from your VPC by configuring a virtual private gateway (VPG) and customer gateway to the VPC, then configuring the site-to-site VPC VPN.
The Need for Secure AWS Connections
AWS Site-to-Site VPN enables secure, encrypted links between on-premises environments and the AWS cloud. It’s an indispensable tool for organizations expanding their data centers, enhancing disaster recovery setups, or exploring hybrid cloud architectures.
AWS network security FortiGate offers comprehensive protection and flexibility in hybrid cloud environments.
Key Features:
- Data Security: All traffic is encrypted, ensuring sensitive information is protected.
- Flexibility: Supports FortiGate AWS integration with various AWS services.
- Scalability: Ideal for growing cloud footprints and multi-region architectures.
Step-by-Step Implementation
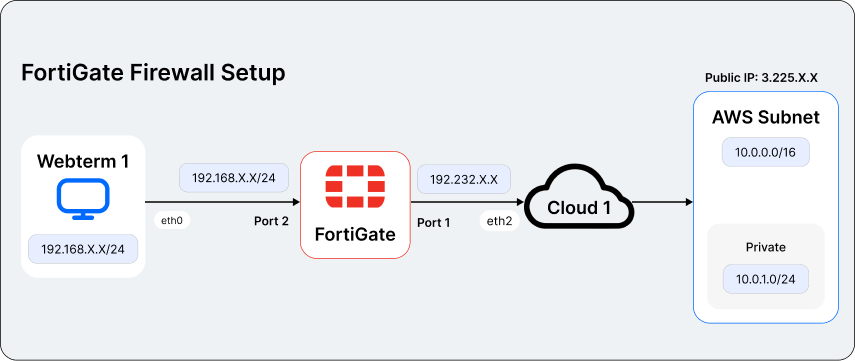
1. Configure Your On-Premises Setup
FortiGate Firewall:
- Configure Port 1 as a DHCP Client for external connectivity and management.
- Assign a static IP
192.168.X.X/24to Port 2 for internal network traffic. - Enable essential services (HTTP, HTTPS, PING) for diagnostics and monitoring.
Web Terminal Setup:
- Set the terminal’s IP to
192.168.X.X/24and connect it to the firewall’s internal interface.
2. Set Up AWS Components
a. VPC Creation
- Open the AWS Console and create a VPC:
- Name: AWS-VPC
- CIDR Range:
10.0.0.0/16
b. Define Subnets
- Add a Private Subnet
(10.0.1.0/24)for internal resources. - Add a Public Subnet
(10.0.2.0/24)for external-facing services. - Attach both subnets to the VPC.
c. Attach Internet Gateway
- Create an Internet Gateway and attach it to your VPC.
- Update the public subnet’s route table with a default route pointing to the gateway.
3. Configure Customer and Virtual Private Gateways
a. Create a Customer Gateway
- Provide your on-premises public IP address.
- Ensure it is tagged appropriately for easy identification.
b. Create a Virtual Private Gateway
- Attach the Virtual Private Gateway to the AWS VPC.
- Update the route tables to include routes pointing to the Virtual Private Gateway for private subnet traffic.
4. Establish Site-to-Site VPN Connection
Link the Customer Gateway and Virtual Private Gateway.
Configure the IPSec tunnel using the AWS-provided configuration file.
Download the configuration file for use in setting up the FortiGate firewall with AWS.

5. Configure VPN on FortiGate
a. Phase 1 Settings:
- Select the VPN Name
- Go to the FortiGate dashboard and navigate to the IPSec VPN section.
- Choose the appropriate VPN connection from the list or create a new one.
- Provide a descriptive name for the VPN to identify it easily.
- Set a Remote IP Address
- Enter the remote gateway IP address provided by AWS.
- This should match the public IP of the AWS Virtual Private Gateway.
- Set Policy and Routing
- Define a policy to control traffic flow:
- Source: Local LAN (e.g., 192.168.X.X/24).
- Destination: AWS subnet (e.g., 10.40.0.0/16).
- Action: Allow.
- Configure the routing table to direct traffic to the VPN tunnel interface.
- Add any additional static routes as required by your network design.
- Define a policy to control traffic flow:
b. Phase 1 Settings:
- Specify the remote AWS Gateway IP.
- Use a pre-shared key for mutual authentication.
- Set encryption details:
- Algorithm: AES-128
- Authentication Protocol: SHA-1
- Key Exchange Group: 2
- Key Lifecycle(seconds): 28800
c. Phase 2 Settings:
- Define the VPN subnet ranges.
- Enable Perfect Forward Secrecy for additional protection.
- Match settings to AWS requirements for smooth FortiGate AWS integration.

6. On-Premise FortiGate Configuration
VPC Tunnel Configuration:
- Configure the tunnel with your
IP: X.X.X.X/255.255.X.X. - Steps:
- Select the VPN name.
- Set a remote IP address.
- Configure policy and routing.
- Set a static IP and interface:
- Enter the pre-shared key.
- Add encryption and authentication settings, ensuring Diffie-Hellman group number 2 is selected.
- Go to Phase 2 and select the subnet as specified in the AWS documentation.
- Add static routes based on AWS documentation.
- Configure firewall policies:
- Interface:
fg_lan 192.168.X.X/24for incoming traffic from the internal network. - Set the outgoing interface to the VPN tunnel.
- Interface:
- For AWS LAN
(10.40.0.0/16):- Set incoming traffic from the VPN tunnel.
- Configure outgoing traffic to the internal network.
7. Finalize and Validate
FortiClient VPN Setup:
- Access the FortiClient VPN URL (Replace with your IP and PORT):
https://X.X.X.X:PORT/remote/login?lang=en. - Configure the connection:
- Connection Name: [Provide your connection name].
- Description: [Add a brief description].
- Remote Gateway (Replace with your IP): X.X.X.X (provided by AWS).
- Authentication Method: Pre-shared key.
- EAP Method: Prompt on login.
- Failover SSL VPN: None.
- Save the settings.
Testing:
- Select the VPN connection and enter your credentials:
- Username: [Your username].
- Password: [Your password].
- Ping the private EC2 instance to validate connectivity.
Conclusion
Configuring an AWS Site-to-Site VPN with a FortiGate firewall not only combines the scalability and flexibility of the AWS cloud with the advanced security features of Fortinet but also establishes a foundation for a robust hybrid cloud architecture. By following this guide, you’ll enable a secure, reliable, and efficient bridge between your on-premises network and AWS VPC, ensuring uninterrupted operations and enhanced data protection.

Author's Bio

Pratik Kasbe is an Infrastructure Engineer at Mobisoft Infotech with a total of 5 years of expertise in designing, implementing, and managing IT infrastructure. He specializes in network management, cloud architecture, system administration, and security. Passionate about leveraging emerging technologies, he excels in automating processes, enhancing system efficiency, and driving innovation in IT operations.


